You’ve got half a dozen passwords for work, encryption keys, and SSH keys — how do you keep them all straight? If you’re on Linux, you have an excellent option in the form of Seahorse. It’s easy to use, and you’ll be able to tackle all your credentials with little effort.
Generally speaking, most average users assume a password is nothing more than something that gets in their way of getting to their “stuff” quickly. Most Linux users, on the other hand, know that passwords are the keys to the kingdom and encryption keys are keys to the universe. Like me, many Linux users have passwords and encryption keys for multiple uses. Because of this, a tool for the management of those keys can make life so much easier. One such tool is Seahorse. Seahorse is the GNOME application charged with managing encryption keys and passwords and I want to demonstrate how both passwords and encryption keys can be easily managed with this tool.
Installation
Although Seahorse was intended to be used on the GNOME desktop, it can be used with other desktops (such as KDE or Enlightenment). However, since Seahorse was created for GNOME it will not properly integrate into KDE applications. That is fine, because encryption and secure shell keys as well as passwords can still be easily managed. If Seahorse is not already installed (It should be found in the Start > Settings menu in KDE and Applications > Accessories in GNOME) simply open up the Add/Remove Software tool, search for Seahorse, and install.
Managing Passwords
Since most all users deal with passwords, the first (and most logical) place to start is password management. Seahorse is an incredible tool for the management of passwords. What can be done?
- Store passwords.
- Remove a password from cache.
- Add details about a password.
- Create a new password.
- Create new password keyrings.
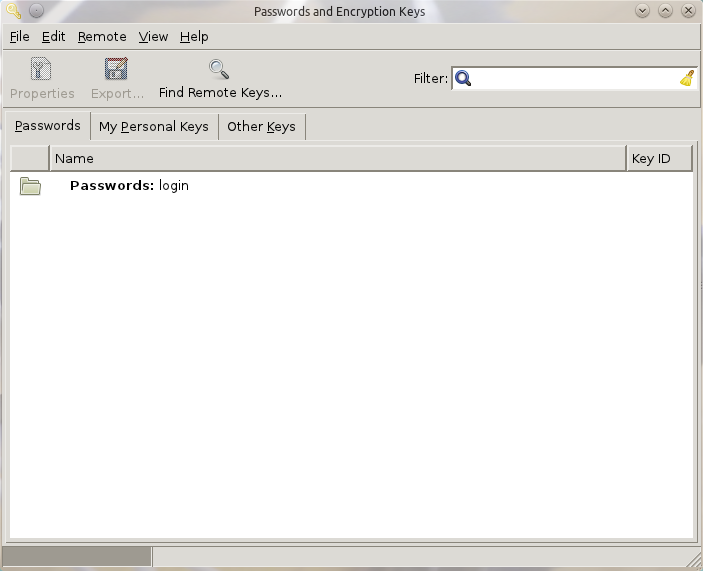
The default keyring is the Login keyring, which is where keys are stored. When Seahorse is fired up it will offer a very simple interface (see Figure 1). From that one main pane, expand the keyring entry to list out all of the various passwords that are stored. This may, at first, seem like a glaring security issue in and of itself, since no password has been entered to reach this point. Fear not, this keyring can be (and should be) locked and unlocked. To lock the keyring, do the following:
More than one keyring can be retained within Seahorse for further expansion.
- Right click the target keyring.
- Select Lock from the menu.
- If you have not added a lock password, add one when prompted.
To unlock the keyring, follow the same steps, only select Unlock and then enter the locking password. It is also possible to change the keyring password, but the old password will be required to to do. If you are going to take advantage of Seahorse, I highly recommend you lock all keyrings with strong passwords.
Adding a password to this keyring will highlight how important it is to have that keyring locked. So, assuming the keyring lives in a locked state, here is the process for adding a password:
- Click File > New.
- From the new window, select Stored Password and click Continue.
- In Add Password window select the keyring this password should belong to from the drop-down.
- Give the password a description.
- Enter the password in the password field.
- Click the Add button.
The password has been successfully saved. Now, to view that password, follow these steps:
- Right click the keyring and click Unlock.
- Enter the unlock password and click OK.
- Expand the keyring to view the newly created password.
- Double click the password entry to be viewed.
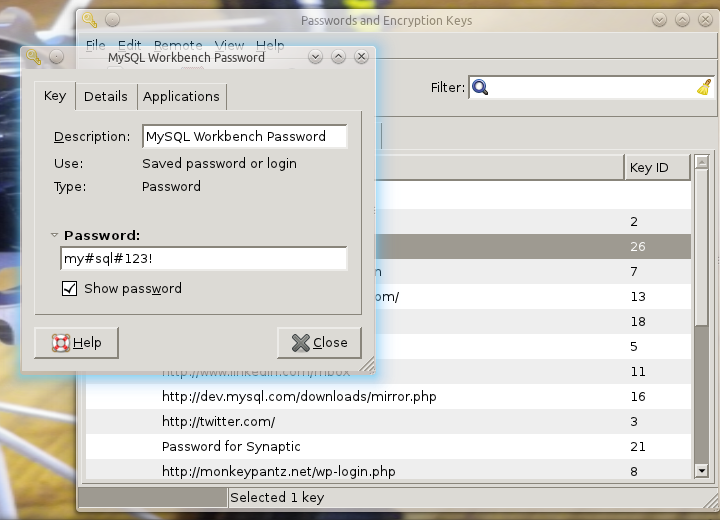
- In the new window (see Figure 2) expand the Password field.
- To view the password check the box for Show password.
The next time this password entry is opened, the Show password check box will once again be unchecked.
Manage Encryption Keys
Encryption keys is where Seahorse really shines. Not only can encryption keys be created and managed from within Seahorse, so to can secure shell keys. These two features along make Seahorse worth using.
In order to create a PGP encryption key, follow these steps:
- Open Seahorse.
- Click File > New.
- In the resulting window, select PGP Key and click Continue.
- Fill out the settings in the new window (Name, Email Address, Comment).
- If advanced options (such as Encryption type, Key strength, and Expiration date) are needed, expand the Advanced section and fill out that information.
- Click Create.
- Type and confirm the passphrase to be used for the key and click OK.
- Do some work on your computer to help with the generating of the random seed and wait for the key to be created.
One that is done, go back to the Seahorse main window and click on the Personal Keys tab (see Figure 3), to see all personal keys managed by Seahorse.
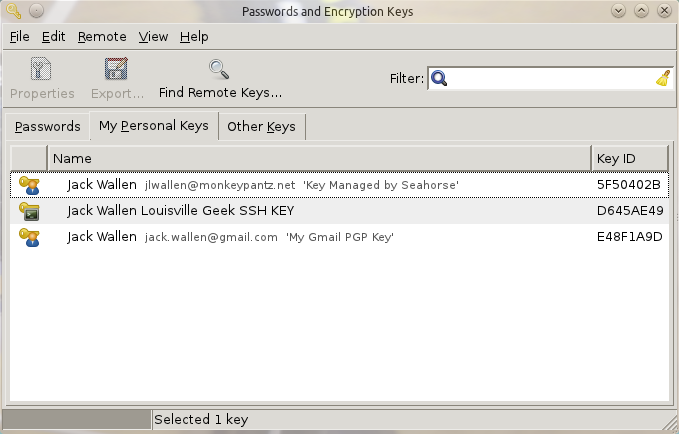 From this tab keys can be signed, exported, and more.
From this tab keys can be signed, exported, and more.
Signing an encryption key allows the recipient of the key to verify the authenticity of the key. To digitally sign a key, do the following:
- Select the key to sign from the Personal Keys tab.
- Click the Sign Key button in the toolbar.
- Fill out the necessary information in resulting window (making sure to select how carefully the key has been checked and the correct signer for the key.)
- Enter the passphrase for the key.
- Click OK.
The key is now signed. It is possible to sign a key with multiple email addresses. But the only addresses available to sign with will be those that are already associated with keys in Seahorse. This can be helpful if more than one key is associated with one user (but different email addresses).
The public keys can also be exported (in the form of .asc files) which can then be handed out to those who need to send encrypted email which can then be decrypted with that encryption key’s private key. These keys should only be handed out to trusted users.
Publishing Public Keys
Many users like to publish their public keys so they are easier to distribute. Seahorse has a built in mechanism for publishing keys (so nothing is really necessary outside of simply creating the keys, signing the keys, and then publishing the keys. To publish keys click Remote > Sync and Publish Keys. From the new window click on the Key Servers button and then, from the Key Servers Preferences window, select the Keyserver the key should be published to (from the drop-down), click Close, and finally click Sync. All keys should then be available on the Keyserver selected.
Managing SSH Keys
Secure Shell is one of the best tools for remotely logging into Linux/UNIX machines because it is far more secure than telnet. But even with that extra security, it’s always best to add yet another layer. This can be achieved with the help of secure shell keys that can be handled by Seahorse. Here are the steps:
- Open Seahorse.
- Click File > New.
- From the resulting window select Secure Shell Key.
- Give the key a description and click Create And Setup.
- Enter (and confirm) a passphrase for the key and click OK.
- In the new window enter the address (IP or FDQN) of the machine to receive the key and the login name on the remote machine.
If all went as planned, instead of a password prompt, a bash prompt should appear ready for work. This, of course, requires that public keys are guarded, otherwise the obvious security hole will make itself quite apparent. There is a known bug in Seahorse that affects some installations and causes the originating machine to not be able to send the ssh key to the target (during creation.) The development team is aware of this bug and will (hopefully) have it fixed soon. If that bug rears it’s ugly head, as a temporary stop-gap, use ssh-copy-id username@address where username is the remote username and address is either the IP address or domain of the recipient.
Practice Safe Computing
The reality is, no matter how many security tools are used, if they are not used wisely those tools will not help much. Even when employing encryption caution must be used to ensure keys do not wind up in the wrong hands. But when encryption is used properly, it is a great tool that will lend a level of security otherwise not found. And, when encryption is needed, thankfully there are tools like Seahorse to make the management of those keys a cinch.