Firewall Builder is one of the most powerful security tools available for Linux. With this user-friendly GUI tool, both simple and highly complex firewalls can be created and managed. With the help of Firewall Builder, every firewall chain can be easily managed rule-by-rule. But without knowing the details of rule management, the task might seem a bit daunting.
To manage rules in Firewall Builder, it is necessary to understand how to:
- Manage multiple items in a single rule.
- Use multiple policies.
- Use branching.
- Manage NAT rules.
- Manage routing tables.
There are a number of features in Firewall Builder that make it easier to organize and manage rules, including:
- Using rule groups.
- Make use of colors to make rule management easier.
- Use find and replace.
- Compile a single rule.
The above list will be addressed, to help make rule management a far easier task.
Multiple Objects In A Single Rule
A nice feature of Firewall Builder is that rules can have multiple objects in each column of the rule. Remember, an object can be a host, and address, services, sources, etc. There are times when a rule needs to apply to more than one object. Say a single rule needs to include two different sources; with Firewall Builder this is simple. What if one machine, on the internal network, needs to allow only two specific machines secure shell access. To do this two rules could be created, but why bother with the extra work? Instead, create source objects for each of the machines that need access and then, once they are created, drag and drop both of those objects into the source section of the rule. Simple.
Multiple Policies
By default Firewall Builder comes with a single Policy object called Policy that holds your filtering rules. One thing that Firewall Builder does that is unique is when rules are added to the default policy the software will automatically determine what type of entries (INPUT, OUTPUT, or FORWARD) needs to be generated (based on what’s in the rule.)
It is also possible to define additional Policy objects, just like adding user chain in iptables, by doing the following:
- Right-click the firewall and select “New Policy Rule Set”.
- Give the policy a name
- Once the new policy object is in place it must be linked to the main policy using the Branch function shown next.
Note that to add rules to the newly defined Policy double-click it in the object to open it for editing in the rules window.
Branching
Having multiple policies is helpful in keeping things segregated — such as having a different Policy for inbound web traffic versus inbound VPN traffic. If a packet reaches a point in the firewall chain the requires it to then be acted upon by a different, specific Policy object, a branch will be necessary. The branch function can send the incoming packets to a specific Policy object, based upon matching criteria, to its proper destination. This is just like using a user defined chain as the target in an iptables INPUT, OUTPUT or FORWARD chain.
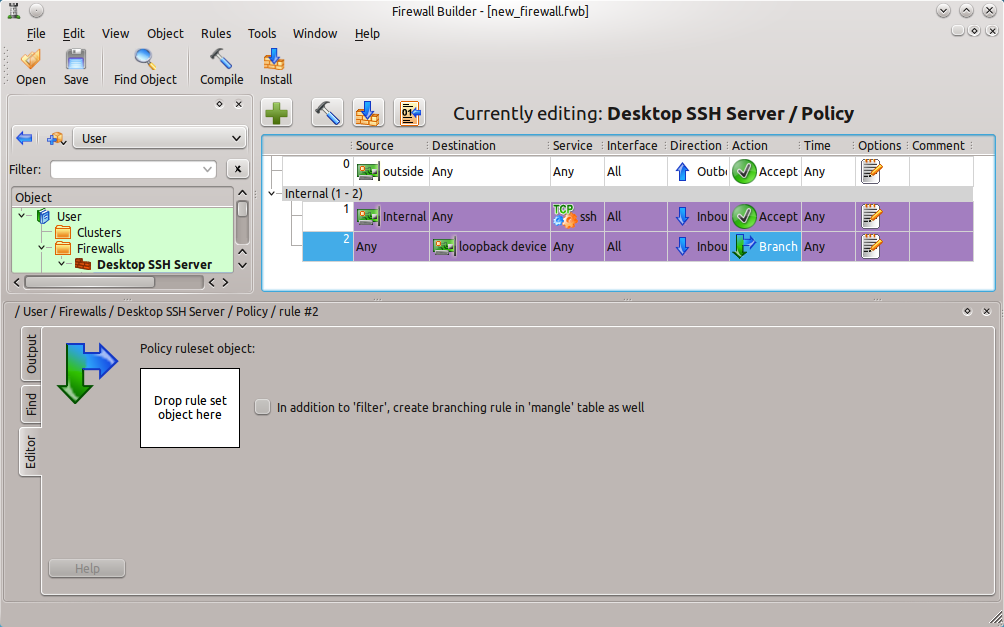
To add a branch in a rule right-click the Action column of the rule and select Branch. When the editor opens up (see Figure 1) the Policy object created earlier can then be dragged and dropped from the left navigation tree into the “Drop rule set object here” box.
You will know if an object can be dropped into the branch if the “+” symbol appears when you try to drop the object into the box.
Managing NAT Rules
Just like the Policy object is used to configure filtering rules, the NAT policy object is used to configure NAT rules. Network Address Translation (NAT) allows IP address rewriting. For example, NAT can be used to allow external sources to gain access to internal hosts that use private addresses (Such as 192.168.1.1.) Since Network Address Translation is handled by the firewall, Firewall Builder is the perfect tool to manage these rules as well.
A NAT rule is created similarly to that of a regular rule, the only difference being that the NAT rule must be created within the NAT policy object. To create this, do the following:
- Expand the Firewall to be worked on.
- Double-click on the NAT object.
- Click on the “+” button to add a new rule to the NAT policy.
- Drag and drop the necessary objects to create the NAT policy.
Creating Network Address Translation rules is made incredibly simple with Firewall Builder.
Managing Routing Tables
It is also possible to manage the static routing tables through Firewall Builder. With this various routes for a machine can be created that will instruct a machine how to reach its destination. In order to manage the routing table do the following:
- Expand the Firewall entry in the left navigation pane.
- Double-click on the Routing entry (see Figure 2.)
- Construct the rules in the same way access policy or NAT rules, using the drag and drop method to place appropriate objects into the rule.
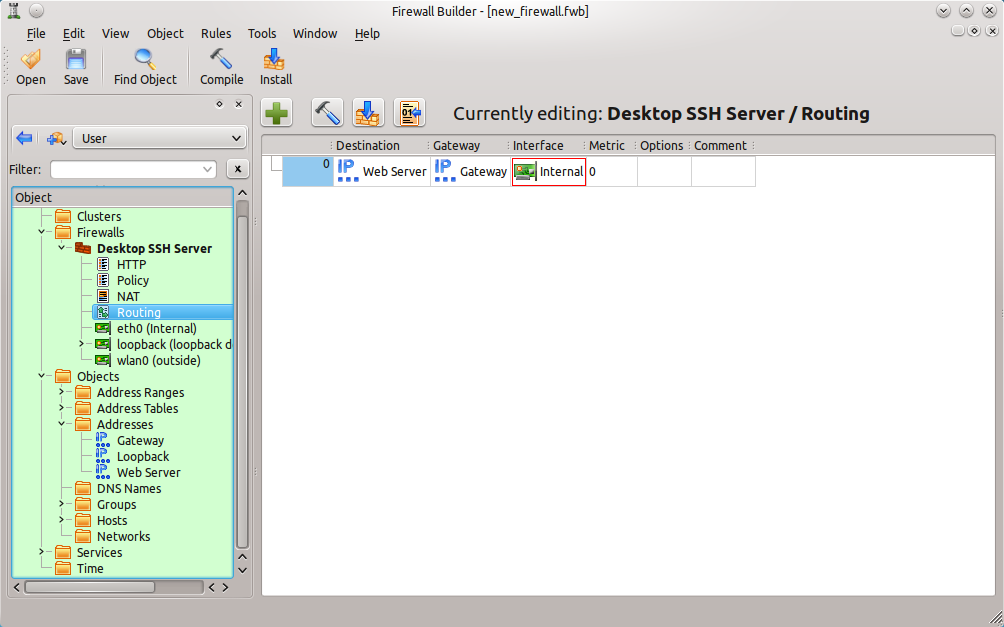 Here is a single routing rule that has been created by dragging pre-configured objects into the necessary columns of the rule.
Here is a single routing rule that has been created by dragging pre-configured objects into the necessary columns of the rule.
For the routing, the following information is necessary:
- Destination: Any addressable object (hosts, addresses, address ranges, groups, networks.) Remember, the default destination (Know as the “Default”) is 0.0.0.0/0.
- Gateway: Can be an IP address, an interface, or a host with only one interface.
- Interface: Specify an outbound interface for packets. It is important to note that this interface must be a child interface of the firewall. Also, this option is not available for BSD firewalls.
- Metric: The metric of the route. Like the Interface option, the Metric option is not available for BSD firewalls.
- Comment: A human-readable comment.
Now that you know how to create and modify different types of rules, let’s look at some ways to organize and manage your rules.
Managing Rule Groups
Groups make life with Firewall Builder a whole lot easier. Groups do not just apply to objects. Rules can be combined into groups to make the managing of rules much easier. For example, to make life easier, two very simple rule groups can be created:
- External
- Internal
Obviously the External group will contain all external rules and the Internal group will contain all internal rules. To add rules to a group do the following:
-
Select the rules to be added to a group (To select more than one, hold down the
Ctrlkey while selecting rules.) - Right-click the selected rule(s).
- Select Add Group
- In the new window, give the group a name.
- Click OK.
This will automatically group all of those rule together and list them in a hierarchical tree view (see Figure 3). When new rules are created that need to belong to the group, simply right-click those rules and then select Add To The Group X (Where X is the name of the group.)
The group name will be listed about the combined rules and can be expanded or contracted to save space.
Coloring Rules
It’s also possible to use colors to help organize the firewall chain more manageable. To change the color of either an individual rule or a rule group, right-click that rule (or group) and select Change Color. This can help easily identify Internal from External rules or rules that pertain only to certain machines, groups of machines, subnets, etc.
Find And Replace
Firewall rule chains can get fairly sizable, so much so they become unwieldy to use. It always helps to know that a tool offers the ability to quickly locate a string of text. Firewall Builder can do just that. When examining a firewall rule set, hit Ctrl-F and the find (find/replace) window will appear. Note that to find an object either drag the desired object into the box where it says “Drop object you want to find here” or type in the name of the object. To replace an object, drag the replacement object to the box “Drop object to replace with here”. It is possible, however, to limit the scope of the search to the tree only, tree and policy of all firewalls, policy of all firewalls, or the policy of only the opened firewall.
Compiling A Single Rule
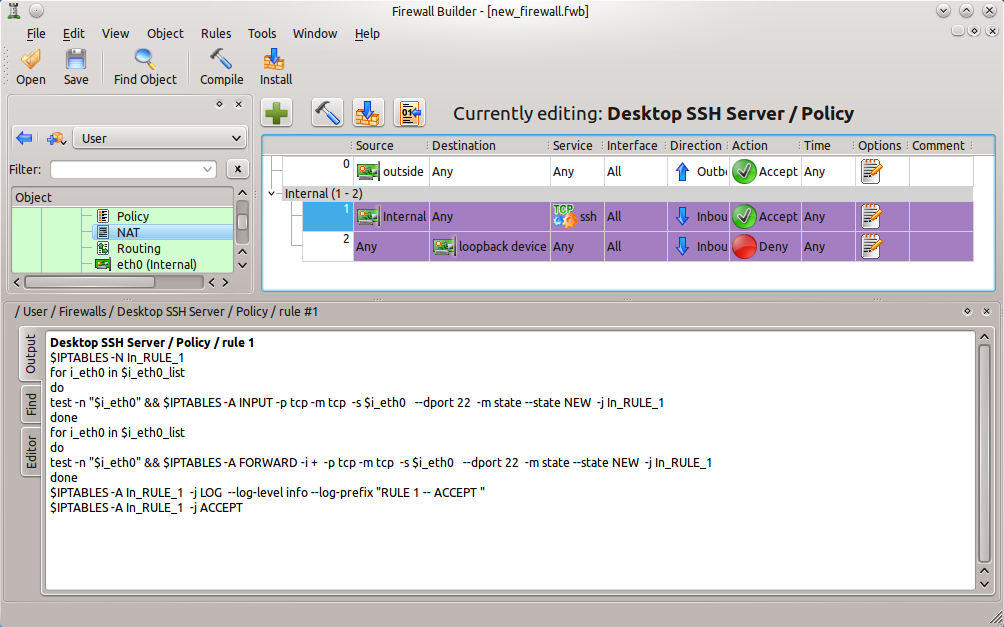
Another really cool feature of Firewall Builder, is the ability to compile a single rule from a chain of rules. Instead of having to compile the entire chain of rules, it is possible to compile a single rule. What this will do is output the compiled rule so it is possible to see exactly what that rule does (see Figure 4.) This is a great way to learn more about the underlying security tool (such as iptables) on a system.
The output in the bottom pane is the result of compiling the single rule (rule number 1 in this case.)
Rules Are Your Friend
Remember, firewall rules are the very heart of the security of a system, so it is imperative they be managed well, understood, and created with care. Firewall Builder is one of the best graphical tools available on the Linux platform for the managing of these rules. Don’t short-change a firewall by neglecting all of the powerful tools included in this package that are there for the sole purpose of helping make rule management a snap.