Firewall Builder is one of the most powerful and user-friendly firewall creation utilities available for Linux. One of the many reasons Firewall Builder is both powerful and easy to use is its objects feature. Objects are reusable elements that can be added and removed from firewall rules by dragging and dropping the object into firewall rules. Firewall Builder comes with plenty of pre-defined objects that can be used right away, and also makes for easy creation of new objects.
Objects are so crucial to the ease of use and understanding of Firewall Builder, I want to dedicate this entire article to the creation, editing, and use of objects. With a sound understanding of objects under the belt, any one should be able to create secure and flexible firewalls to fit nearly any need.
Standard Library Predefined Objects
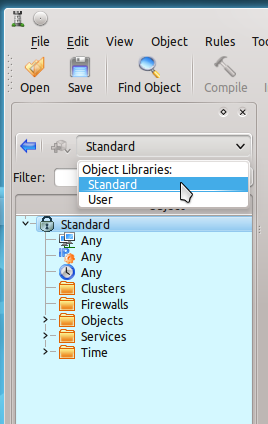
Firewall Builder stores objects in what are known as Libraries. By default Firewall Builder includes two Libraries.
- Standard: The predefined objects that can be dragged and dropped into firewalls. These objects can not be edited.
- User: An empty pre-categorized library where users can add their own objects and then drag and drop them into firewalls.
To select a library, click on the Library drop-down (see Figure 1) and select either the Standard Library or the User Library. Let’s say, for example, the firewall being created will be used to secure an HTTP server. Why bother creating TCP/UDP service objects when they already exist in the Standard Library? Simply open up the Standard Library (click the Library drop-down and click Standard), expand the Services entry, Expand the TCP entry, and the HTTP and HTTPS entries will be available. Drag and drop all of the related entries necessary for the new firewall into the desired rules for the firewall.
Another way to find the object is to use the convenient filter feature, located just below the Library drop down, that lets you quickly filter the objects in the tree to find what you are looking for.
It is also possible to create a Custom Library by clicking the drop-down to the left of the Libraries drop-down and selecting New Library.
In my previous article I discussed how to create objects specific to firewall used for SSH connections into a host. The methods discussed in that article describe the creation of objects for the User Library. One of the nice features of Firewall Builder is that those objects can be then reused in other firewalls. So even if the objects were initially created for the SSH firewall, they can then be re-purposed for a firewall focused on a Web server. That doesn’t just apply to services; any of the objects created in a previous firewall can be re-used over and over.
Object Types
Don’t think objects are limited to services or addresses. In fact quite a few object types can be created and used, and here is a listing of the types:
- Address Ranges: A range of addresses can be configured into a single object.
- Address Tables: This is an address-based object that can be created when a range of addresses is needed but the actual addresses are not known when the firewall or policy is being written. The Address Tables object has an added feature which allows for the object to be loaded at either compile time (during firewall compilation) or during run time (when Firewall Builder runs the firewall script). More on this in a moment.
- Addresses: A single address that can be used for an interface, source, or destination (such as a host).
- DNS Names: This object represents a DNS “A” or “AAAA” name and resolves to an IP address during either compile or run time. What this highlights is the intelligence of the compiler and its ability to resolve addresses to names during compilation.
- Groups: A group is a container that holds references to multiple objects of the same or similar type (Addresses, Address Ranges, Network Objects).
- Hosts: A host object represents hosts on a network: Desktops, Workstations, and any other network node that has a network address.
- Networks: This object describes an IP network or an entire subnet.
Object Groups
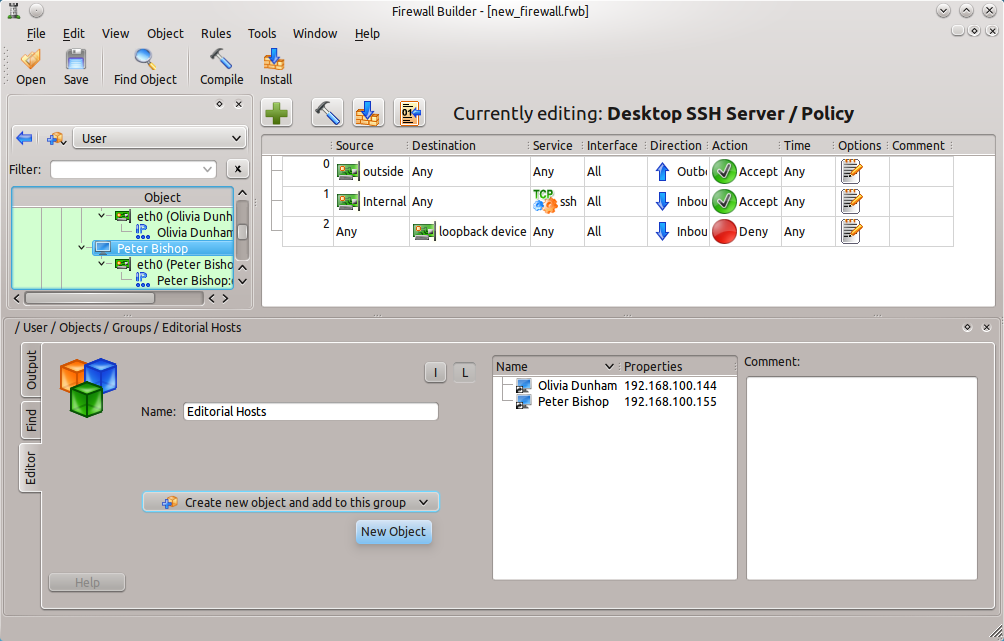
A group is a container that holds references to multiple objects of the same or similar type (Addresses, Address Ranges, Network Objects). When a new group is created (see Figure 2) the member objects can either be created from within the configuration of the group itself (click the “Create new object and add to this group” drop-down) or objects can be dragged and dropped into the group from one of the Libraries. During compile time the Firewall Builder compiler will determine if a group should be expanded and multiple chains needed or if a single chain can take care of the group.
Make sure the name given to the group adequately describes the purpose of the group so that group can be re-used without having to examine its contents.
Address Tables
Address Tables are incredibly handy. Essentially this object allows you to define a list of addresses and/or networks into a rule, even if the actual addresses are unknown at the time the rule is created. What must be done, however, is (when the addresses are known) a file is created that will house the addresses. That file name and location is configured into the Address Tables setup (see Figure 3).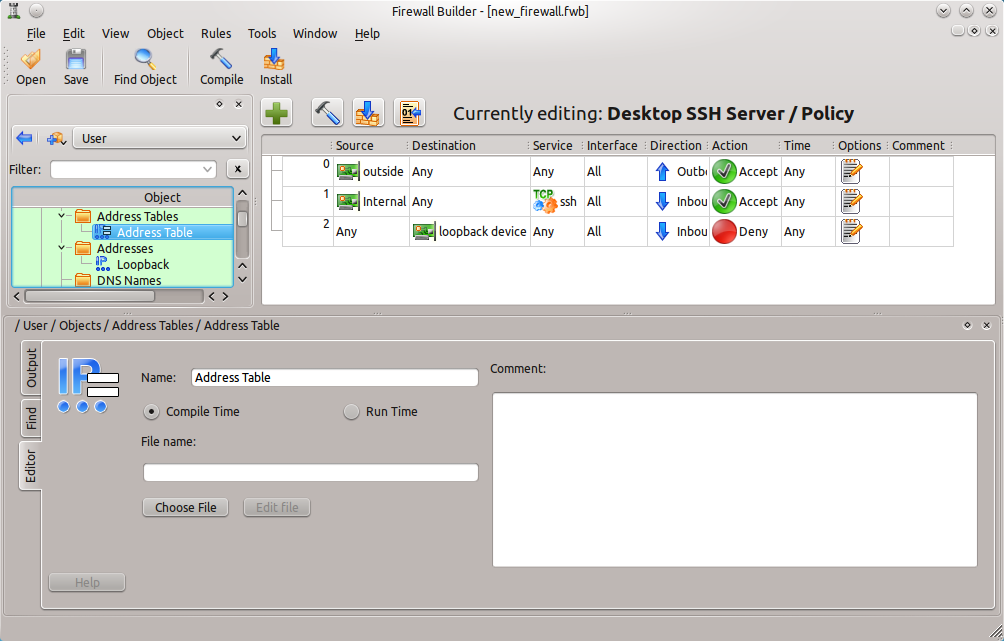
To configure the file the addresses will be read from click the Choose File button and then navigate to file.
When you have configured the Address Table to be aware of the file containing the addresses, it is also possible to directly edit the file from within Firewall Builder. To do this click the Edit File button and the Firewall Builder Script Editor will open (see Figure 4).
Figure 4
fwbuilder_script_editor.png
You can create a file using the script editor, just enter the full path to the file and click Edit. The file will be created when you click Save.
Services
The services objects are all fairly self-explanatory (Custom, Groups, ICMP, IP, TCP, UDP, Users). The only Service that may need explanation is the TagServices. The TagServices object allows packets to be tagged by one rule and then acted on by another rule. Packet tagging is fairly complex. Essentially a TagServices object is created and configured with either a tag number or string. To match a tag in a rule just drag and drop the service object to the Service column of the rule. To create a rule that sets the tag, set the Action to Tag and drag and drop the TagService to the bottom of the screen where it says “Drop object here.”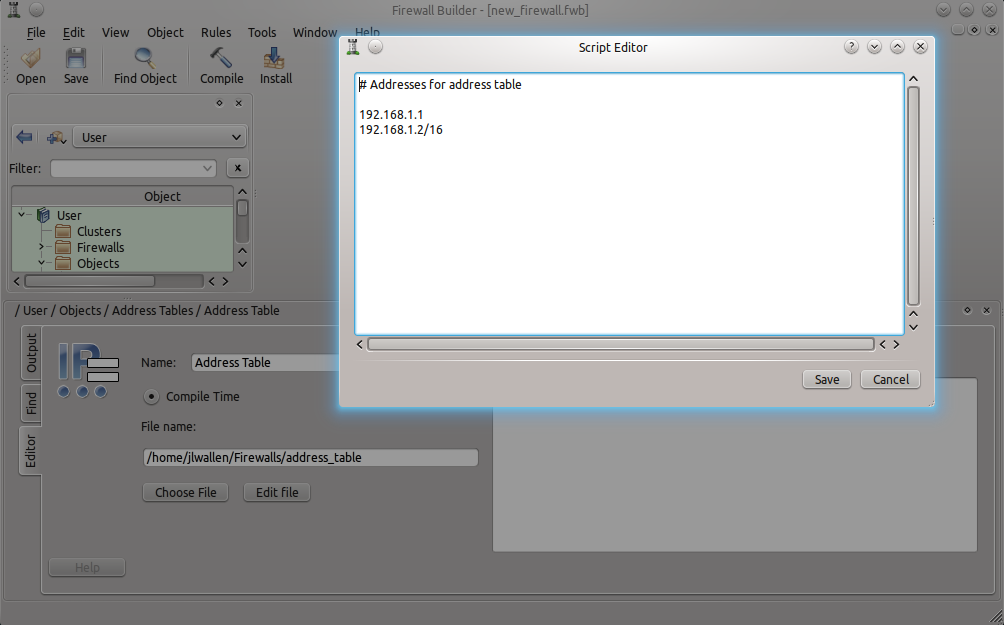
It is also important to know that TCP and UDP Services can have definitions for both source and destination ports configured and that if a configuration of 0 is used all ports will be matched. Say, for example, it is necessary to create a service for HTTP using port 8080 as the destination, but a specific source port is not necessary. To do this enter 8080 as the destination port and leave the source port as is (set at 0).
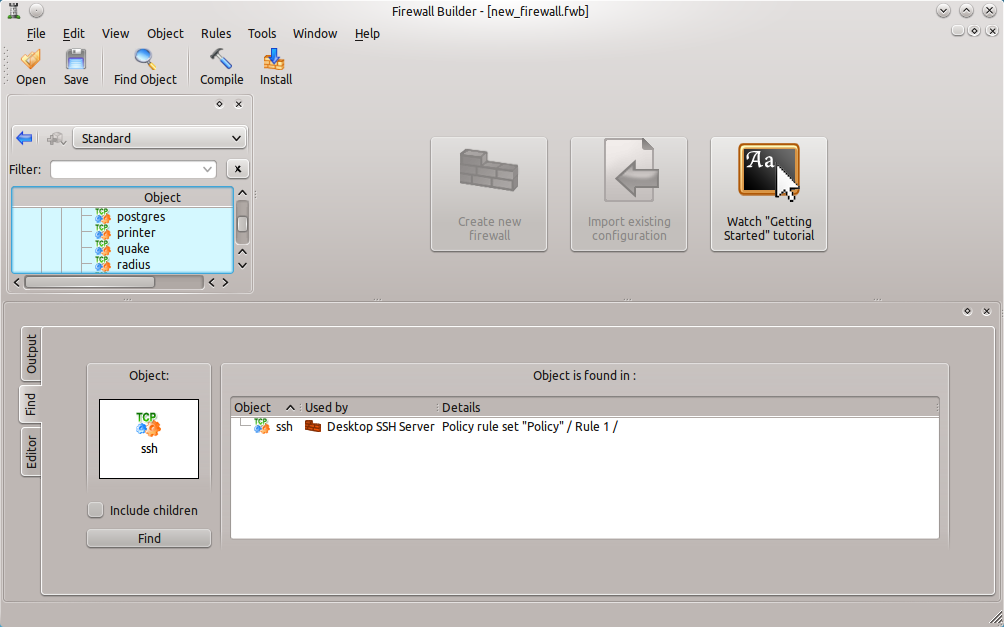
A handy trick to know is how to locate where a service is being used within a firewall. With a firewall open, navigate to a service (either from the Standard or User Library) and right-click the service. When the context menu opens select Where Used. A pane will open in the lower half of the Firewall Builder window (see Figure 5) that will, upon clicking the Find button, display where the service is used within the firewall. This is especially handy when trying to troubleshoot a particular firewall.
If any child services were created from the original, make sure to search for those as well.
Building Blocks
The creation and manipulation of objects serves as the foundation and building blocks which all firewalls are created within Firewall Builder. Because objects make the creation of firewalls more efficient and user friendly, it is important to understand how they can be best utilized. When used correctly, Firewall Builder objects help to make the administration of firewalls a far easier task.