Last week we looked at managing rules in Firewall Builder. In the last installment of our series on Firewall Builder, I’ll take a look at managing firewall settings with the Firewall Builder.
We’ve covered quite a bit already about Firewall Builder This week, I want to open up the Firewall Settings window to illustrate how much further a Firewall can be flexed, stretched, and configured — all from a single, user-friendly window.
Getting To The Settings
As should be expected, getting to the settings window is simple — so long as it’s not overlooked. What I’m talking about is not the Firewall Builder Preferences. The settings I am referring to actually apply to individual firewalls. So, in order to reach the settings window, a firewall must be open within Firewall Builder. Once the firewall is open (double click on the firewall to edit it), look for the Firewall Settings Button (see Figure 1).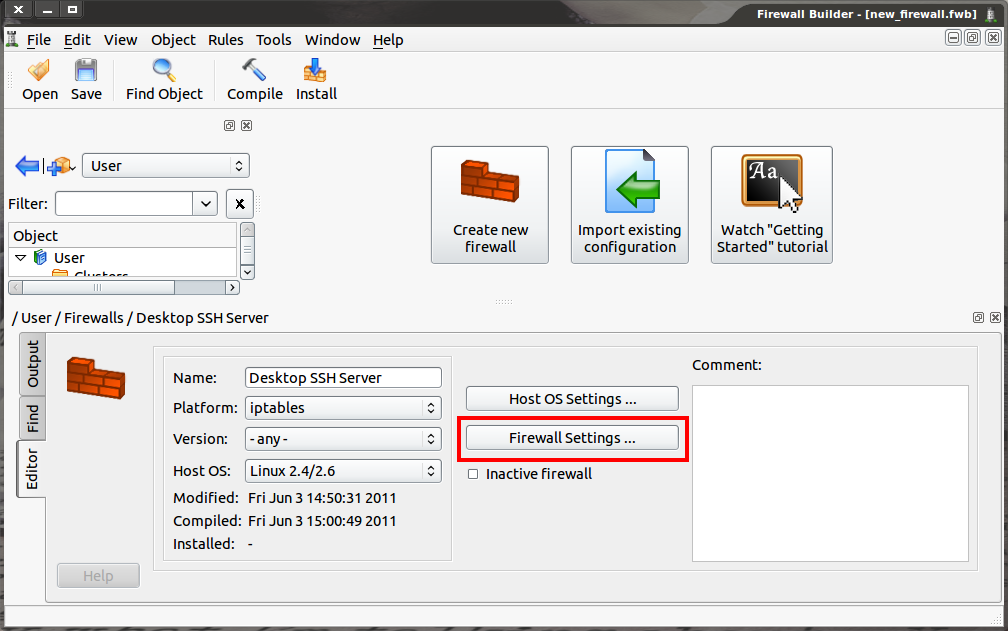
When the Firewall Settings button is clicked, it will open the settings window only for the currently open firewall.
The Firewall Settings button is located near the center of the window. Click that button to get to the settings in question. Let’s examine this window, tab by tab.
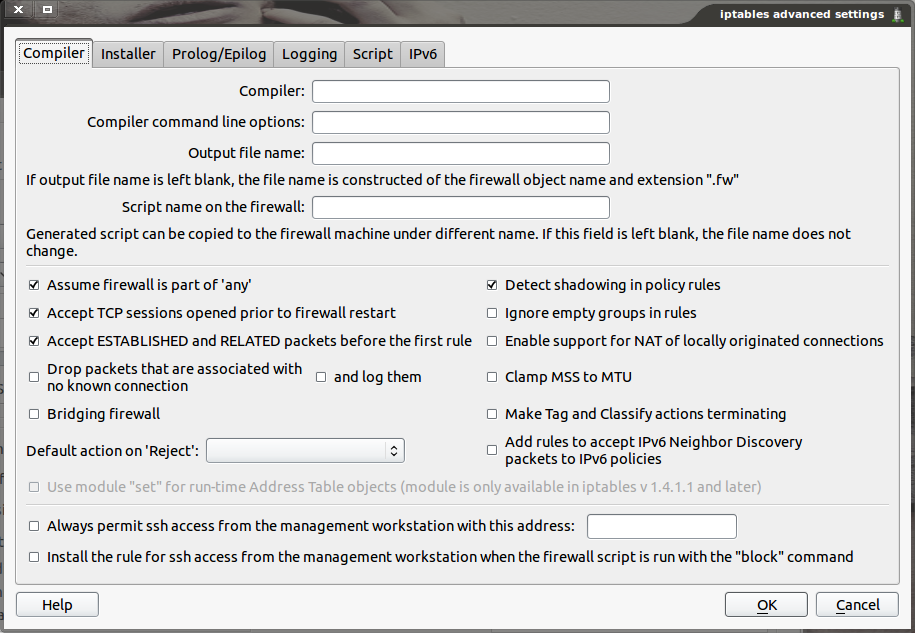
Compiler Tab
The compiler tab (see Figure 2), as the name implies, deals with the compiling settings for the firewall. There are a few options, in particular, that I want to point out. The first option is ‘Assume firewall is part of “any”‘. If this option is checked, rules that are configured with “Any” in the Source or Destination fields will also generate rules for traffic destined to or from the firewall. In iptables this will result in a rule being added to either the OUTPUT or INPUT rule chain.
The configuration options here will be automatically compiled into the firewall in question.
Another important option is ‘Always permit ssh access from the management workstation with this address’. This helps prevent situations where a user cuts off their access to the firewall because there isn’t a rule allowing SSH access to the firewall itself. If this option is enabled, enter either a single IP address or a network using CIDR notation (e.g. 192.168.1.0/24). When the firewall is compiled, Firewall Builder will automatically add a rule permitting SSH access to the firewall from this IP address or network at the top of the generated rules.
Installer Tab
The Installer Tab has three settings that you should pay close attention to. The first is the option “Directory on the firewall where script should be installed”. This should match a directory that exists on the firewall where the firewall script should be run. Typically for iptables firewalls the directory is either /etc/ or /etc/fw (if this directory has been created on the firewall).
The second setting to pay attention to is the username. This is the username that will be used when Firewall Builder connects to the firewall to install the generated firewall script. If the username configured in the installer tab does not have administrative rights, the installation will fail. So in this section, enter a username that does have admin rights and can actually install firewall rules (if the user can use the iptables command, that user most likely has rights enough.) If the username setting is left blank the user will be prompted to enter the username when they run the install wizard.
Finally, in the installation tab, there is the additional command line parameters for both ssh and scp options. This is an incredibly helpful should ssh and/or scp use alternative ports. Should that be the case, simply add something like -p 2222 to instruct ssh to use non-standard port 2222 (instead of standard port 22).
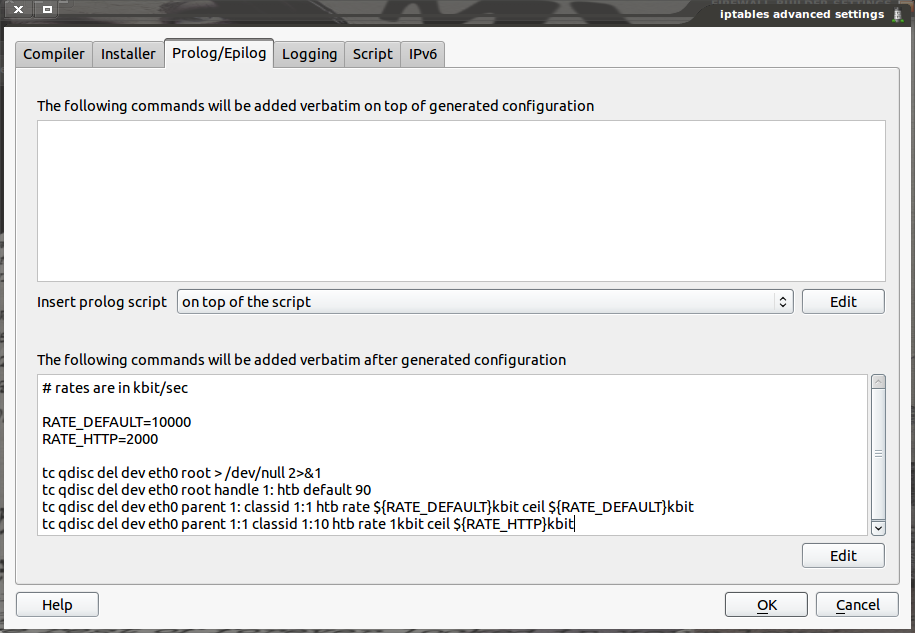
Prolog/Epilog
The next tab that should be of use is the Prolog/Epilog. This tab allows for the addition of script commands in bash format to be added either to the beginning or to the end of a firewall script. For example, the amount of traffic being served up by an HTTP server can be controlled by using the Traffic Control command (tc). The commands would need to be added to the epilog (end) of the firewall as shown in Figure 3.
Prolog scripts can be added in three different locations, whereas Epilog scripts can only be added to the end. Make sure that the commands entered can be run as a bash shell script without any errors.
Script Tab
Finally, the Script Tab offers a number of setting options, of which there are four settings to pay close attention to. It is important to note that this tab directly effects the script generated for the firewall being configured and not the machine that Firewall Builder is running on. The first is “Configure Interfaces of the firewall machine.” If this option is not checked the script generated will not include shell code necessary to manage IP Addresses. By default this is on.
The next option in the Script tab is for VLAN interfaces. If the checkbox for “Configure VLAN interfaces” is checked the script generated by Firewall Builder can create and remove VLAN interfaces for the firewall. If left unchecked, this feature will not be available. In other words, if VLAN interfaces are necessary, make sure this check box is checked. This same option is available for bridged interfaces. If the firewall to be installed needs to configure any bridge interfaces, the check box for “Configure bridged interfaces” must be checked, otherwise bridged interfaces will not be available to the firewall machine.
Finally, “Use iptables-restore to activate policy” is the last option I will deal with. There are two ways in which generated scripts can be loaded:
-
Using
iptablescommand: This command will load the rules of a firewall one at a time. -
Using
iptables-restore: This command will activate the rules of the firewall all at once.
The biggest difference between the two methods, with regard to Firewall Builder, is that the iptables-restore is a much faster process. This can make a significant difference when the firewall becomes longer and more complicated. If, on the other hand, a firewall is short and basic, the standard method of running iptables commands line-by-line will work just fine.
Keep Digging
I have only scratched the surface of the Firewall Builder Firewall’s Settings window. Although I have touched on many of the more important options, it would behoove you to comb through all of the tabs to make sure there aren’t options available that would make a difference in a particular firewall. But the settings options illustrated here are those that most users will want to at least examine for their firewall rules, before they are compiled and installed.