Author: Joe Barr
Defcon 15 followed hard on the heels of the Black Hat Briefings last week. Black Hat closed at Caesar’s Palace on Thursday evening, and Defcon started at the Riviera Friday morning. Both shows are the creation of Jeff Moss, but while Black Hat is aimed directly at the professional side of network security, Defcon is all about community, mad fun, hacking, and games.
The price of entry reflects that difference. The Black Hat Briefings cost $1,695 at the door, cash or charge. Entry to Defcon is $100, cash only. While feds and security pros of all kinds attend both shows, the Defcon crowd is generally younger and wilder, with the hair styles, tats, and piercings to prove it. Early on in this year’s show, unofficial estimates were that the crowd would be down slightly from the 7,000 reported for last year’s event.
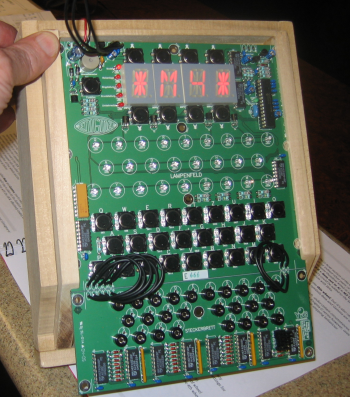
Classic badgetry
Last year’s conference badge was impressive, but Joe Grand, a.k.a. Kingpin from L0pht Heavy Industries, outdid himself with this year’s creation. It features a programmable, scrolling LED display with a 16-character buffer. A full page of the conference guide is dedicated to explaining how to program and operate it.
The only problem with this year’s design is that the circuitry on the back of the card is completely exposed, so shorting and inadvertent input were a constant annoyance, especially since it takes a while to get the text and scroll speed just right if you want to program a personal message. Optionally, you can leave the default text: “I (heart) DEFCON XV.”
The original idea for the badges was to prevent counterfeiting, but I think the fun factor in the design, creation, and usage has come to outweigh that aspect.
Dateline vs. Defcon
The biggest buzz-maker at Defcon 15 was the aborted undercover journalism attempted by NBC News’ Dateline. Defcon’s press liaison Niko Sell told journalists in the press room prior to the 10 a.m. opening on the first day that the organizers had received a tip — some say from a mole at Dateline, others say from a federal agency — that Dateline was going to send a reporter in to covertly record hackers’ secrets at the show. This sort of thing is strictly prohibited at Defcon, and journalists are required to sign an agreement that clearly states that no recordings or pictures can be taken of attendees without their express consent.
A photo of the Dateline reporter was circulated among Defcon staff and displayed at each presentation so she could be spotted and tailed. Eventually, the organizers turned the game around on her. First they offered the reporter — Michelle Madigan, an associate producer of Dateline — press credentials, but she declined. Then they tipped her to a supposed unmaking of a covert federal agent which was supposed to occur during “Spot the Fed.”
Instead, Defcon founder Jeff Moss explained to the crowd on hand for the session that there was an undercover reporter in the room, and suggested they might want to play “Spot the reporter” instead of “Spot the Fed.” That was enough to get Michelle out of her seat and scurrying for the door — but not quickly enough to evade the horde of attendees and journalists who followed her, videotaping every step of her hasty withdrawal. Final score: Defcon 1, Dateline 0.
Pick a skybox
There are about a dozen smaller rooms — skyboxes — ringing the Royale Pavilion below where the game, snack, and vendor areas are located, which are used for special interest presentations at Defcon. Just as I got inside the one on lock picking, an attractive blonde handed me a wooden box containing a blinking electronics kit she had just finished assembling and informed me it was a working model of an Enigma machine, the famous German crypto machine of World War II. Pretty cool.
All around the room, attendees were working on picking door locks, with varying degrees of success. Then one of the presenters announced they were going to close the room down for an hour or so while most of them went down to the game area below and tried to win a lock picking contest. I said that I had accidentally locked myself out of my Mercedes, and asked if anyone could help me get back in it, but got no takers.
The worst presentation of either show
I arrived in the hall where Bruce Potter was scheduled to hold forth on “Dirty Secrets of the Security Industry” about half an hour early in order to be sure I could get a seat. The panel under way when I got there was debating disclosure.
It was a bad presentation at last year’s Black Hat, and it hasn’t improved with age. The term “full disclosure” has been hijacked by vendors — hardware, software, and security — and neutered of any real meaning. Not only that, they have been pushing for the term “responsible disclosure” to take its place. Responsible disclosure evidently means anything not embarrassing to them, so that their lies, coverups, inaction, and legal actions go unmentioned and unchallenged.
Raven Alder — an independent researcher and Black Hat/Defcon speaker — spoke up from the audience to note that she had been silenced more than once by vendors’ serious legal threats if she disclosed a vulnerability, thus reinforcing remarks made at Black Hat by Jeff Moss during the First Annual Pwnie Awards.
One attendee asked why corporate behavior and ethics were being mentioned in the same sentence, prompting one of the panelists to speak for a few minutes about how ethical corporations really are, and how Enron had been a rare aberration. I admired how cleverly he had conflated two nonequivalent concepts — ethics and legality — to silence any criticism of corporations for their zero-ethics policies, but was otherwise unimpressed. Skilled, professional liars have been a part of the computing scene for a long time.
Dirty secrets
After the disclosure panel left, the hall filled to overflowing for Potter’s presentation. The room was packed and the exits were blocked, as were the lanes between and around the seats. A goon known as Priest (Defcon staffers are called goons) had to encourage part of the overflow crowd to leave the room before the fire marshal cleared the entire conference area before Potter’s presentation could get underway.
Priest, by the way, is a large fellow, and reputedly is a current or former intelligence operative, fluent in Mandarin Chinese. He had a pretty busy Defcon, judging from what I saw of him at the show. The last time I had seen him was in 2004, when he was first silencing and then protecting an anarchist speaker from angry attendees who didn’t share his political views.
I saw Priest again briefly in the YouTube video linked to above, as he introduced Dark Tangent at this year’s “Spot the Fed” session. But the most memorable view of Priest at Defcon 2007 may be a photograph in the conference guide. Unconfirmed sources have told me that the barely visible nude-but-modest male image on page 6 — the Got Pr0n? page — is actually Priest, thanks to the Photoshop artistry of (name deleted in the interest of national security).
When he was finally able to begin, Potter, the founder of the Shmoo Group and a senior associate at Booz Allen Hamilton, proved to be a polished presenter who knows how to point, pivot, and project. Unfortunately, his rambling style and the time he lost while organizers got the audience down to a legal size kept him from fully covering the topic he wanted to talk about, but he did manage to make a couple of important points. He said one of the most popular mantras of the security industry — defense in depth — is completely bogus. If security problems are the result of bad code or design, the solution is not to be found in expensive Band-Aids. He also noted that you can’t train everyone. He said that no matter how much training you give your people, it only takes one untrained person, a new hire or someone without the gray matter required to comprehend the training, to open the gate or leave it unlocked. Potter also asserted that full disclosure is dead — there is too much money involved for such transparency to be allowed to exist.
Please, no decaf
I got involved in this year’s eighth annual CoffeeWars contest after reading about it on the Full-Disclosure mailing list. Organizer Foofus briefed me on the rules, and also kindly provided the history of the CoffeeWars in the sidebar.
I brought a pound of Ruta Maya Organic Medium Roast coffee beans with me as my entry, and watched Foofus and others set up the table, grinders, and brewing equipment before the doors officially opened at 10 a.m. The judges obviously have fun judging the contest, but they were also pretty serious about their coffee.
The crowd around the table seemed a little larger each time I went by after the doors were opened, and by the time the organizers started packing up a couple of hours later, they had pronounced CoffeeWars 8 a success. Results will be posted on the CoffeeWars site, Foofus says, when he gets around to doing it.
Summing it up
I was there only for the first day of Defcon, which formally closed on Sunday. After the nearly full week of exposure to security pros that the Black Hat Briefings and Defcon represent, I was left with a sense of growing discontent from within the industry. I heard such discontent from Jeff Moss over the legal antics of vendors choosing to silence researchers. Becky Bace, one of the most respected names in the field of information security, is also unhappy with the stink. Raven Alder made her point from the audience during the Disclosure panel, and Bruce Potter wrote the message loud and clear at the start of his talk: trust nobody. Not even — or perhaps especially — the security industry.
Categories:
- News
- Security
- Events