Author: Luigi Paiella
Last month the TrueCrypt Foundation released TrueCrypt 5.0, which finally introduces a Linux GUI for the cross-platform encryption application. TrueCrypt 5.0’s numerous other enhancements include a Mac OS X port, XTS operation mode, the ability to encrypt a system partition or drive under Windows, and the addition of the SHA-512 hash algorithm.
The binary downloads for Linux used to be tailored specifically to each different Linux distribution version, but are now reduced to just two: openSUSE (x86) and Ubuntu (x86). The new TrueCrypt design is no longer affected by upgrades and updates to the Linux kernel. That’s good news for users of other distributions as well, who must still manually compile TrueCrypt from source, but won’t need to do so after every kernel change.
Installation on Kubuntu 7.10 went flawlessly, but the process doesn’t create an item in the KDE menu. It’s surprising that a version meant to enhance usability skips that simple step in one of the most-used Linux desktop environments. Similarly, the .tc file extension seems not to be linked to TrueCrypt. Both things happen on Windows by default.
TrueCrypt can create a hidden encrypted volume inside a standard encrypted one. As it’s impossible to know if a hidden volume exists (hidden volume data cannot be distinguished from the random data normally filling the free space of a standard encrypted volume), this option helps you in situations in which you may be forced to reveal your password. See also Plausible Deniability in the TrueCrypt documentation.
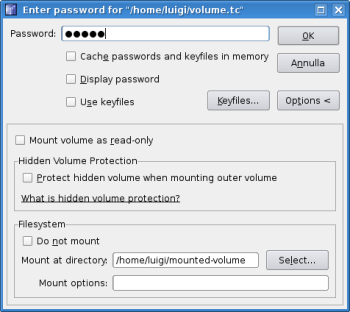
Once you issue the truecrypt command through a console or by typing Alt-F2, both the main window and a tray icon show up. Creating encrypted volumes is simple. Press the Create Volume button to start the TrueCrypt Volume Wizard, and choose the options presented in the different steps: simple or hidden volume, partition or file container, encryption algorithm type (AES is the default) and hash algorithm (RIPEMD-160 by default), password (for which more than 20 characters is recommended), eventual filesystem options, and format.
TrueCrypt for Linux can encrypt an entire hard disk partition (or entire disk) or a file-hosted volume. Such virtual volumes are stored as a standard file, belonging to any filesystem, but host an independent encrypted virtual disk device.
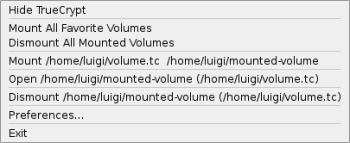
To access existing volumes, choose one of the free “slots” in the main window (slots correspond to the available unit drive letters on Windows and predefined mounting points in Linux), select the file or partition containing your encrypted volume, and press the Mount button. You’ll be prompted for the volume password; insert the standard or the hidden volume password depending on which volume you want to mount. If the volume password is correct, you’ll be prompted for the root password.
Since version 4.3a, TrueCrypt no longer supports the set-euid root mode of execution and requires you to enter the administrator password through the sudo command. Although this is helpful from a security point of view, it makes using TrueCrypt on a multiuser workstation difficult. By editing the sudoers file with visudo, you can allow users belonging to a specific group (let’s call it, for example, “truecrypt”) to execute TrueCrypt with administrative privileges but without knowing the root password. Just insert the following row:
%truecrypt ALL=(root) NOPASSWD:/usr/bin/truecrypt
This method works equally well with the older command-line version. Your mounted volume will then be available in the position /media/truecryptX, where X is the number of the slot you chose at the beginning, unless you specified an existing mount point in the Mount Options page.
Although TrueCrypt 5.0 can open volumes encrypted through 64-bit block-encryption algorithms such as Blowfish, CAST-128, and Triple DES, it doesn’t let you create new volumes with algorithms that are weaker than 128-bit block-encryption algorithms such as AES, Serpent, and Twofish.
The speed difference between accessing an on-the-fly encrypted volume and an unencrypted one is evident and particularly noticeable when copying large files on older computers. On an Athlon 1200 system the time required to complete a copy was almost doubled. Nonetheless, even on a so slow computer, you can still watch decrypted-on-the-fly, fullscreen, compressed videos without particular issues.
Once a volume is mounted, you can add it to your favorites. TrueCrypt keeps the volume position and mount point in a Favorites menu so that next time you’ll need to provide only the correct password. In addition, you’ll be able to mount, dismount, and open your favorite volumes in Konqueror simply through the tray icon’s right-click menu.
If you create an encrypted partition or volume on a removable drive, you can access it from a different computer or different operating system (Windows, Mac OS X, and Linux). Of course, you need to be sure that the second operating system supports the filesystems used by the first. TrueCrypt also has a Traveler mode (available for Windows) to automatically start TrueCrypt or mount a specified TrueCrypt volume when the ‘traveler disk’ is inserted in Windows, without the need of installing the software.
You can still run TrueCrypt’s command-line mode in version 5.0 through the -t switch, which needs to be specified as the first option. Unfortunately, the syntax has not been kept consistent with previous versions, and you need to answer more questions, such as what the eventual keyfile and hidden volume will be, before being able to mount your volume. Furthermore, when version 5.0 was first released, trying to use TrueCrypt in a pure console environment, even with the -t option, ended the program with the following error: “Error: Unable to initialize gtk, is DISPLAY set properly?” This was particularly annoying if you had no access to a graphical interface. Luckily, TrueCrypt Foundation corrected that problem one week later with the release of TrueCrypt 5.0a, which lets you use the console version of the utility properly.
The TrueCrypt Web site provides comprehensive documentation (which is almost entirely replicated in a PDF file included in every installation package), a FAQ page, and a forum with a dedicated Linux section. Solutions for distribution-specific issues usually can be found elsewhere on the Web.
TrueCrypt’s new GUI proves more effective than the previous command-line version, because the tray icon speeds up the most frequent actions, especially if you automate TrueCrypt startup at login by adding a link into KDE Autostart folder (add the --background-task option to have it iconised by default).
Although TrueCrypt’s license is open source but not GPL-compatible, version 5.0a is one of the simplest and safest cross-platform encryption utilities available.
Categories:
- Reviews
- Tools & Utilities
- Security