You can never be too careful when connecting your computer to the outside world. The first and most important line of defense for any Linux system is the firewall. This software tool erects a barrier, hence the name firewall, at the point of entry to your computer which typically means your network connection to the Internet. In reality this could be a wired or wireless Ethernet connection or even a dial-up modem.
The trick to setting up a firewall correctly is to keep out the bad stuff and let the good stuff in. This essentially involves configuring specific rules to allow or disallow network traffic over specific ports. All network traffic on a typical PC happens over the same IP address but through certain ports depending on the type of traffic. There are a number of well-known ports used by specific protocols such as port 80 which is the default port for all HTTP traffic. Other commonly used ports include 110 for pop3 (incoming e-mail) and 25 for SMTP (outgoing e-mail). You can find a list of these ports on the iana.org website.
There are other ports such as 42 used by services like the Windows Naming Service (WINS) that you need to enable if you want to browse a Windows-based network. Samba (SMB and CIFS) uses ports 137-139 while https uses port 443. Many secure e-mail channels will use https to move data, so you’ll need to make sure port 443 is open for that purpose. The bottom line is you need to do a little reading and have a good understanding of the kinds of things you want to do in order to properly configure your firewall.
Tools
The Netfilter/IPtables project is all about providing a software packet filtering framework deeply integrated with the Linux 2.4 and 2.6 kernels. Deep kernel integration is needed to enable a method for watching every packet that traverses the network stack from the point it comes in through the hardware interface. This makes it virtually impossible to get any packets past the filter unless they are explicitly examined and allowed. A stateful packet inspection also makes it possible to combat attacks consisting of malformed packets.
IPtables is the actual command line configuration tool that determines how packets are filtered by the kernel. It works by setting up a set of rules that allow or deny traffic over specific ports and protocols. Other utilities include IPset for configuring, enabling and disabling rule sets of a complex nature. IPset makes it possible to easily block incoming individual IP addresses or entire ranges. This type of tool can be used to help combat denial of service (DOS) attacks by blocking the traffic completely.
Ubuntu
The default firewall configuration tool distributed with the most recent Ubuntu distributions is ufw. According to the help file, ufw is a program for managing a netfilter firewall. It’s essentially a command line tool which allows you to configure the rules that will be used by the IPtables package. By default, ufw is disabled so you will have to turn it on explicitly if you want to use it.
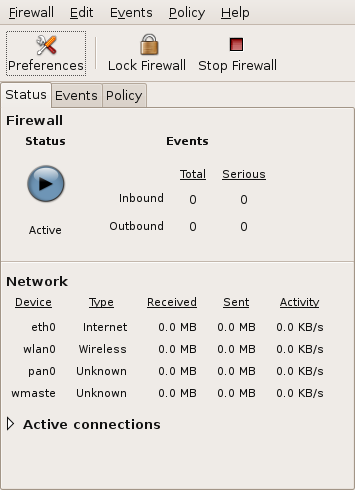 Firestarter is a popular GUI-based firewall tool available for Ubuntu. It uses a simple wizard-based approach to configuration and startup. Once the firewall is running you get a nice control panel (see Figure 1) that minimizes to the top status bar area on the desktop. The main page shows the current status of all active connections, amount of traffic on all the network devices and any events detected. You can also start or stop and lock the firewall with a single click. A preferences tab presents you with all the different configuration options in a nice dialog interface.
Firestarter is a popular GUI-based firewall tool available for Ubuntu. It uses a simple wizard-based approach to configuration and startup. Once the firewall is running you get a nice control panel (see Figure 1) that minimizes to the top status bar area on the desktop. The main page shows the current status of all active connections, amount of traffic on all the network devices and any events detected. You can also start or stop and lock the firewall with a single click. A preferences tab presents you with all the different configuration options in a nice dialog interface.
openSUSE
Configuring the firewall in openSUSE takes place using the YaST tool. YaST allows you to configure the different network interfaces on your machine separately. That means you could have a very strict set of rules for your wireless interface, since you tend to use that when you’re on a public network, and a very lax set of rules when connected through the wired interface (shown in Figure 2). You can also change these settings on the fly when necessary.
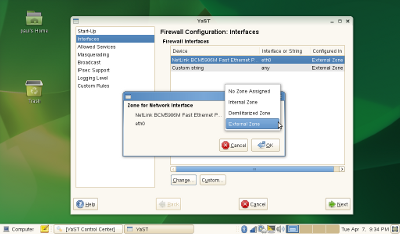 YaST also uses the concept of zones to make it easy to quickly configure an interface for a pre-defined set of rules. The strictest zone is “External”, meaning you are connecting to an outside network using the interface. For a typical home network behind a router with a firewall you might go with the less restrictive “Internal” zone. The third option is the DMZ or de-militarized zone. This is typically used in corporate environments where you want to give access to certain types of information to the outside world but not directly to your internal corporate network. In this case you have a computer with multiple network connections to act as a proxy to an internal application or database.
YaST also uses the concept of zones to make it easy to quickly configure an interface for a pre-defined set of rules. The strictest zone is “External”, meaning you are connecting to an outside network using the interface. For a typical home network behind a router with a firewall you might go with the less restrictive “Internal” zone. The third option is the DMZ or de-militarized zone. This is typically used in corporate environments where you want to give access to certain types of information to the outside world but not directly to your internal corporate network. In this case you have a computer with multiple network connections to act as a proxy to an internal application or database.
Firewall Appliances
Something slightly stronger would be appropriate for the small to medium size business with many machines on an internal network and a single connection to the Internet. In this case you would want to configure a standalone device as a firewall to give an extra measure of protection to your company resources. There are a number of Linux-based firewall appliances created just for this job. Each has its own strengths and weaknesses, but all are designed to be loaded on a single computer with at least two network connections.
Endian is a distribution designed as a Unified Threat Management (UMT) security appliance. It features application-level proxies for all the standard protocols along with such things as e-mail SPAM filtering, anti-virus protection and a VPN solution based on OpenVPN. The Linux Embedded Appliance Framework or LEAF is another distribution targeted at a single purpose firewall appliance.
For the home environment there are replacement firmware packages for some of the popular devices such as the Linksys WRT54G. OpenWrt is one such package that brings a whole host of new capabilities to this best-selling device. Other solutions in this category include m0n0wall, IPcop, and IPnuts. You can also find a number of VMware-based appliances on their website.
Bottom Line
Firewalls provide your computer or network protection from any number of potential threats prevalent on the Internet. At a minimum you need to turn on your computer’s firewall with at least the default settings. An even better solution would be to know what ports you need to open for the applications you need to run. Then only open those specific ports to the outside world.


