Author: Ben Martin
It is good practice to use a different password for each Web site you need to log in to. Good passwords tend to be long and contain a wide selection of characters. That can make remembering all your passwords difficult. But you can make things easier on yourself by storing passwords for various Web sites in an encrypted file on your computer. I’ll take a look at a four programs that give you easy access to your passwords when you need them and protect the password file itself against compromise.
Of course, storing passwords on a computer introduces a degree of risk. The program might be buggy, the cryptography library used by the program might be buggy, and you are effectively lumping all of the passwords that you store in the encrypted database into the same security bracket — that is, if the encrypted database is compromised, the attacker will probably be able to use any password contained in it. One the flip side, by using a single very strong password to protect 50 Web site login credentials, you don’t have to keep memorizing new strong passwords every time you access a new site. Still, you might not ever want to store the password you use to authenticate with your bank.
I looked at KeePassX, Password Dragon, Password Gorilla, and JPasswords, most of which allow you to store not only user name and password information but also the URL associated with this key and other metadata — information you can refer to collectively as credentials. Generally the credentials are stored into a single file, perhaps referred to as the credential database, which is encrypted prior to being saved to disk. As a disclosure, I have been using KeePassX to store passwords for a while, but I have tried not to have any bias toward KeePassX in this article.
The key used to unlock the credential database can be a combination of a password and a file containing encryption keys. Generally, having an encryption key file is of no use unless you also know the password to unlock it as well. Which combination of password and encryption key file you use generally depends on how severe the impact of disclosing the credential database is. If you are using a separate encryption key file, you might like to store that key file on a secure flash drive so that it is physically separate from the machine that stores the encrypted credential database.
KeePassX
KeePassX can encrypt your credentials database using either AES or Twofish, and includes implementations of these algorithms with the source code.
KeePassX is not in the distribution repositories for Fedora or Ubuntu, but it is available as a 1-Click install for openSUSE 11, Fedora 9 for both 32- and 64-bit, and 32- and 64-bit packages for Ubuntu Hardy. KeePassX is also available for Mac OS X, Windows, and Maemo. The main dependency of KeePassX is the Qt library.
KeePassX can use a combination of password and key file to protect your credential database. Selecting “New Database…” from the File menu brings up the dialog window shown below. If you use an external encryption key file, that file will contain 64 bytes of ASCII characters.
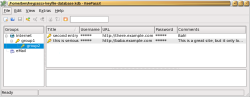
You can group your credentials, and each group can itself have subgroups. A group also has an icon associated with it to allow you to quickly find the credential you are after in the main treeview shown below. There are about 70 icons available with KeePassX, or you can use an custom image of your choosing.
Because the credentials include a URL, the context menu for each credential includes an option to open the URL in a browser. The context menu for a credential also includes options to copy the user name or password to the clipboard using Ctrl-C and Ctrl-B respectively.
Copying a password to the clipboard poses a few security risks. Apart from the fact that any program that can read the clipboard can sniff your passwords, you have a password in the clipboard until you next copy to the clipboard. The preferences for KeePassX let you set up a timeout so KeePassX will automatically clear the clipboard when the timeout expires. This helps to solve the latter problem by only having the password available for, say, five seconds in the clipboard. You can also set a timeout to lock KeePassX itself after inactivity for a given number of seconds.
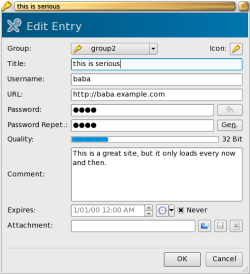
The credential editing dialog is shown below. You can configure whether a password should be visible by default. Leaving it obscured is handy for laptop use where you might want to see the full details of a credential without potentially exposing the password to an onlooker.
Password Dragon
Password Dragon is a Java application and requires version 1.5 or later of the Java Runtime Environment. Cryptography uses the Blowfish algorithm and is handled by the BlowfishJ library. Once you have a JRE installed, the below commands will get Password Dragon up and running:
$ unzip /.../passworddragon.zip $ cd passworddragon $ java -jar passworddragon.jar
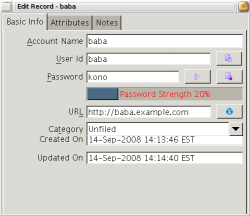
The main interface is shown below. You can add up to 10 custom attributes to each credential, which will be displayed in the details view shown toward the right of the screenshot.
Password Dragon includes support for categories, which let you group your credentials and use the category during searches to limit the results. For example, you could create finance and social networking categories to help you find only the credentials relevant to the task at hand. A category cannot be nested inside another, and each credential can be associated with only a single category.
Password Dragon’s preferences allow you to set whether the Account Name, User ID, Password, URL, Notes, and Category are masked in the Main Table and the View Record dialog. You can set an inactivity timeout in minutes and elect to automatically copy the User ID or Password to the clipboard when you perform a URL launch. You can clear the clipboard on exit, but not after a specified time has passed after a password was copied to the clipboard.
Password Gorilla
Password Gorilla uses the Twofish algorithm to encrypt its credentials database. It is packaged in Ubuntu Hardy Universe but not for Fedora 9 or openSUSE 11. Password Gorilla uses Tclkit, which is available as a 1-Click install for openSUSE but is not packaged for Fedora 9. The Tclkit Web site offers builds for ARM and x86 architectures in both 32- and 64-bit. Password Gorilla is also available for Mac OS X and Windows. The below commands will install and execute Password Gorilla on a Fedora 9 machine.
$ cd $ mkdir ~/password-gorilla $ cd ~/password-gorilla $ cp /.../tclkit-linux-x86_64.gz . $ gunzip tclkit-linux-x86_64.gz $ chmod +x tclkit-linux-x86_64 $ cp /.../gorilla-1.4.kit . $ ls -lh -rw-r--r-- 1 ben ben 246K 2008-09-14 14:32 gorilla-1.4.kit -rwxr-xr-x 1 ben ben 2.2M 2008-09-14 14:32 tclkit-linux-x86_64* $ ./tclkit-linux-x86_64 gorilla-1.4.kit
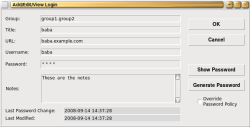
Password Gorilla has no support for external key files and currently supports only a password-protected credential database. You can tell Password Gorilla to lock itself after a given number of minutes of inactivity. There are no options to clear the clipboard automatically at any time, but you can clear the clipboard manually from the Edit menu. The details for a credential are shown in the screenshot.
JPasswords
JPasswords uses Java and requires version 1.4 or later of the JRE. There are two main downloads of JPasswords: the normal version and the deluxe version, which includes some additional look and feel files. JPasswords lets you store a password-protected credentials database but does not support external key files for encrypting your credentials database. JPasswords uses Twofish in CBC mode to encrypt the credentials database.
Once you have a JRE installed, you can start JPasswords by executing java -jar jpws-deluxe-0-5-0.jar.
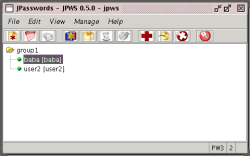
JPasswords supports automatic locking after a nominated period of minutes have passed without activity. You can also have JPasswords automatically clear the clipboard after a given number of seconds so you don’t accidentally leave a password there after copying it to your Web browser. JPasswords supports groups, but you cannot nest a group inside another group. The main window is shown in the screenshot.
The two top items in the context menu for a credential are Password to Clipboard and Username to Clipboard. The three items in the toolbar of the details window are to “Copy the password to clipboard,” “Copy username to clipboard,” and to “Clear clipboard.”
Final words
If you have a mobile device with a Java runtime then JPasswords will give you automatic clipboard-clearing functionality and has no dependencies other than the JRE and its jar file. If Tclkit runs on your embedded platform of choice then Password Gorilla is also easy to install and get running. The interface for Password Gorilla is quite compact so should work well on embedded targets, with the context menu for a credential allowing you to quickly copy the username, password, and URL to the clipboard. If Qt is available on your platforms then KeePassX will integrate well with KDE 4 on your desktop while still working on smaller targets like Maemo.
In a future article I plan to cover two other alternatives that you may already be familiar with: gnome-keyring and KDE Wallet.
Categories:
- Reviews
- Tools & Utilities
- Security
- Desktop Software