If you are new to the Linux operating system, then the whole of Linux security will be untapped territory to you. If you are migrating from Windows, you are most likely accustomed to the standard Firewall/Virus Protection/Malware Protection combinations. You’re used to paying for security and you’re used to that feeling of panic that sets in every time a new virus is released into the wild. The idea of security might have been one of the biggest selling points for Linux to you… and rightfully so.
By default you will have far fewer issues with security with Linux than you do with Windows (if you have any). Why is this? There are two major reasons: design and saturation.
Although many will argue this, by design, Linux is a more secure operating system. Any user can install a Linux desktop distribution and feel fairly confident that, out of the box, their experience will be free from viruses, mal ware, and other malicious code for the life of that installation. Does this mean the new Linux user should ignore all security on their system? No.
Why? Because that new user will eventually gain experience and that could eventually lead to a Linux system administrator ignoring crucial security needs. So it is best to have an understanding of the tools used to compliment a Linux installation (be it desktop or server) with solid security.
Some would argue the only reason Linux has yet to suffered from the same bombardment of viruses that Windows suffers from is because of saturation. Because there are fewer Linux installations many would say those writing the viruses write their malicious code for the Windows operating system simply because there are more Windows machines out there.
This mindset forgets the incalculable number of Linux machines running across the planet. How many Apache servers out there? Did you know that Apache (running on Linux)  is the most widely used web server? Yet Apache, running on the Linux operating system, is not the primary target of viruses, worms, trojans, and rootkits.  
This primer will introduce you to the basic tools used for Linux security. The tools we will illustrate range from command line tools to full-blown graphical tools and from network security, to system security, to user-level security. We will begin with Network security.
Fundamentals
Let’s first examine just why Linux is more secure than most other operating systems. It’s useless to make a blanket statement without backing that statement up with examples and facts.
First and foremost, the Linux operating system was built, from the ground up, with networking in mind. From the very beginning Linux was created to be a multi-user, networked operating system. With that in mind Linux had to be built with a solid foundation in security. To gain that level of security the Linux operating system was developed with a strong system of permissions that applies to both directories and files. Every file and directory on your Linux system has a specific set of permissions that allow (or not allow) you do one of three things:
- Read
- Write
- Execute
For example: Without executable permission a user can not execute a file. To better illustrate this let us look at the /usr/sbin directory. This directory consists of applications that can only be executed by the root user. If the standard user does not have the root user password they can not execute applications or scripts within that directory. Even applications, written for Linux may be written in such a way that they do not have executable permission within the /usr/sbin/ directory. When written like this, a Linux application has a harder time doing damage to a system. It’s all about permissions.
Another fundamental reason the Linux operating system is secure is that it ships with all ports closed. If you’re not sure exactly what a port is you can think of a port as a destination for a specific networking protocol. For example port 80 is the address used for web traffic. By default all of these ports are closed so networking traffic can not gain access to your machine.
Network Security
Although the heading “network security” can fall into any of the three categories, this primarily targets data packets coming and going from a machine. In Windows terms you would be looking at firewalls, packet sniffers, and vulnerability scanners. Granted the end-user will most likely only deal with firewalls, it’s good to know there are other tools available. Let’s begin with firewall tools.
Starting from the “ground up” you have the command line tool iptables. The iptables tool is a complex system that allows administrators to block and route network packets as they see fit. Iptables works by creating chains of rules that, as a whole, create a filter table. As a network packet comes into the system it is compared against the chains in the table starting at the top. The packet passes through the entire table until it either passes all the way through or one of the chains in the table matches the packet and acts accordingly.
Iptables is a very powerful system. That power comes with a price… complexity. Mastering iptables can take time and most end-users have no desire to spend the amount of time necessary to master such a tool. To that end there are graphical front ends that make building firewalls much easier. Most of these front ends use iptables as their underlying system. One of the best of these front ends is Firewall Builder.
Firewall Builder
Firewall builder, as the name implies, builds firewalls. How it works is by using objects to create a firewall specific to your needs. You can either hand build these firewalls or you can use the user-friendly wizard to create a firewall based on a more generalized criteria. As you can see, in Figure 1, there are seven basic templates to choose from. These templates range from a single host (server or desktop) firewall to a firewall for a three-interface server connected to a DMZ subnet.
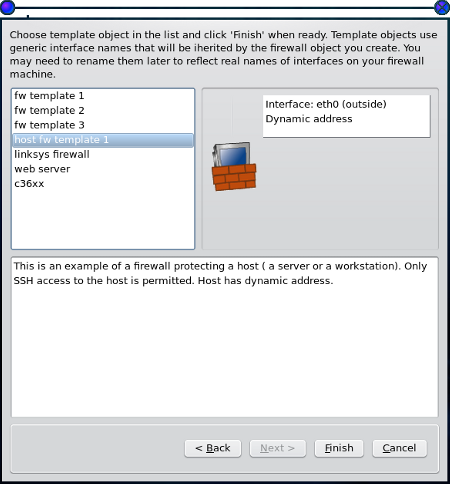
For the typical desktop firewall you would choose the “host fw template 1”. Once you have gone through the wizard you then have to compile the rules and then install the firewall. This isn’t as difficult as it sounds. There is a “Compile” button and an “Install” button. First click the “Compile” button and, once that is complete, click the “Install” button. You’re done.
Webmin
To take the idea of the graphical user interface one step further leads you to the Webmin tool. This tool is a sort of one-stop-shop for administration tools. It doesn’t offer quite the amount of features that Fwbuilder is, does not have nearly the difficult a learning curve as the command-line only iptables, but is much easier to use than any other option. The only catch is you have to install Webmin on your system and know how to get to the interface (http://localhost:10000 usually works well.) What Webmin offers is an iptables module that makes creating a firewall very easy.
As you can see in Figure 2, adding, deleting, and moving rules to a rule chain is simple with the Webmin interface.
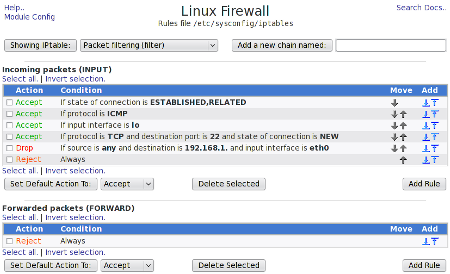
The Webmin tool should make the creation of firewalls very simple. You will also notice, in the Webmin tool, other security modules available such as:
- Kerberos: Network Authentication Protocol.
- Bandwidth monitoring: Monitor bandwidth being used.
- TCP Wrappers: Filter access to network protocols.
System Security
There are a number of utilities, tools, and designs used for system security. We mentioned one of the fundamental system security tools earlier–permissions. Along with permissions comes the fundamental design–the role of users in a Linux system. Recall the mention of the root user? The root user is the administrative user and can execute any task on the system. Gaining access to the root user requires the root password.
To get to the root user issue the command “su” (for “super user”) from the command line. You will be prompted for the root user password. Now, some distributions, such as Ubuntu, employ the sudo system. Sudo comes from “super user do”. Sudo users are given special privileges and can issue most administration tasks simply by using their own passwords.¬†
Beyond that there is one very powerful tool developed by the National Security Agency (NSA) called SELinux (Security Enhanced Linux). SELinux works by creating a system of security that keeps the user from doing any harm to a system (so long as that system has has been locked-down by SELinux). This SELinux enhanced system makes an ideal environment for enterprise computing, mission-critical servers, home desktops, and everything in between. SELinux creates a such a secure environment because, once locked odnw, the tools that could be used against your machines can not do the damage they would normally be able to do.
Not all Linux distributions ship with SELinux. The following distributions take advantage of SELinux:
SELinux is also supported (but not always installed by default) by the following distributions:
User Level Security
Many users aren’t comfortable using a computer, no matter what the operating system, without having anti-virus, spam filters, and root kit checkers. Fortunately there are tools for that. If you are interested in installing such tools you can look at:
- ClamAV for your anti-virus needs.
- SpamAssassin to keep your machine spam free.
- Rootkit Hunter to check your machine for root kits.
Final Thoughts
Hopefully you now have a better understanding of Linux security. You can see there are multiple levels of security that come together to form a solid, secure whole. With Linux you can make your machine as secure as if it were running behind the wals of the NSA itself.



