Author: Cory Buford
Network Security Toolkit is one of many live CD Linux distributions focusing on network monitoring, analysis, and security. NST was designed to give network security administrators easy access to a comprehensive set of open source network applications, many of which are among the top 100 security tools recommended by insecure.org.
NST’s latest version, 1.8.0, was released last month. While previous versions were based on Fedora Core 5, this new release is the first to be based on the Fedora 8, using Linux kernel 2.6.25.6-27.fc8 with Fluxbox as the desktop environment of choice. You can download NST as a live CD ISO or as a VMware virtual machine from the author’s site.
When booting from the live CD, you will be presented with several predefined boot options depending on the service or hardware requirements. The default selection is “desktop/laptop,” which includes all the NST utilities, USB support, and a serial console. All of the predefined boot options need a DHCP server for the network interface to work properly. If a DHCP server is not present, you must manually enter the necessary boot parameters without the DHCP client option. The boot process takes a minute or two, and, for security reasons, you must enter a new root password before proceeding to the command line. From there, users can activate Fluxbox if they wish with a simple command, startx.
You can install NST on a hard drive, but the process is not straightforward. For enterprise network deployment, since permanent NST stations are necessary to monitor real-time network activity and security, hard drive installation is a must.
NST’s virtual machine format gives you a flexible option when you want to test or run the distribution on a machine with lots of resources. The only drawback of this approach is that, since VMware considers a wireless network adapter to be an ordinary Ethernet card inside the virtual machine, wireless card usage is limited.
Inside NST
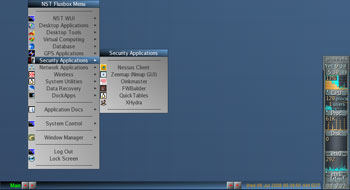
Don’t let the simple look of NST’s FluxBox desktop fool you. Although the interface is plain and simple, a lot of powerful network tools are at your disposal. Among the network penetration testing and analysis tools included here are Kismet, Snort, AirSnort, NMAP, and Wireshark. Nessus, a popular vulnerability scanner, which is not included on the latest BackTrack release (BT3) is included in this distribution. Network monitoring tools like Nagios, Argus, and Zabbix are also included to help you keep an eye on your network’s health. In addition to its network administration tools, the distribution hosts applications for email (Pooka), chat (Pidgin), Web browsing (Firefox), text and graphics editing and processing (ImageMagick, XPDF, Nedit, and others), antivirus (ClamAV), terminal communications (GTKterm, Minicom), remote desktop (VNC, TSClient), and data recovery (cfdisk, Partition Image). I was surprised to find that this distribution includes the free GPS navigation program GPSDrive. Both MySQL and PostgreSQL databases are both included, and, if you need an email server, so is Sendmail.
To use the different tools of NST, you can either use its Web user interface (WUI), which is based on AJAX and JSON, or select each tool from the NST Fluxbox menu. If you know what you’re looking for, just right-click anywhere on the desktop to display the NST Fluxbox menu, with all the tools categorized according to usage. For example, all GUI-based tools used in testing and checking system vulnerabilities can be found on the Security Applications submenu, while tools for general networking, such as Wireshark, are located under Network Applications. One minor concern about the NST Fluxbox menu is that some of the tools appear in multiple categories; for example, you can find the same ATerm application shortcut in the NST WUI and Desktop Applications groups.
If a tool is not GUI-based or requires CLI for its configuration, NST simplifies everything by placing it in the WUI. You can choose either a simplified WUI in which the tools are grouped according to their intended tasks, such as sniffing, monitoring, or penetration testing, or, if you already know what tool to use, you can get it from the categorized tools index.
Using tools with the WUI is simple. Upon selecting a tool or task you will be presented with the tool’s page, on which you can click a button to run a specified script either for configuration or operation. If you need to customize the options, you can easily edit the necessary configuration files associated with the tool or enter command parameters. A description of each tool as well as documentation on its usage is included on its page.
Testing NST
After exploring all the tools available, I set up an NST station probe and deployed it on our office network. Using the hard drive installation procedure, I installed NST on an unused Dell PowerEdge 2500 server with a 1GHz Pentium III processor, 768MB of RAM, three 10/100 NICs, and two 18GB SCSI hard drives.
I first set some of the options, such as IP address, and enabled services like SSH, HTTPS, and VNC. Since one of the major features of this distribution is its WUI, I used that to configure the ntop tool and Zabbix to check network traffic and examine the health of some of the server hosts.
Configuring ntop is a breeze. Just go to the NST WUI and click its Network category link. You will then find ntop on the Monitor subcategory. Clicking ntop will bring you to its configuration page. Select the NIC that is connected to the network to be monitored, enter other ntop options if necessary (I used the default settings), and click the Start button to enable ntop. The WUI shows you the command that was used to enable ntop. Return to the previous page and click “Use ntop interface (HTTPS)” to enter the monitoring page. On ntop’s monitoring page, you get a clear view of network traffic, its different types (TCP, UDP, ARP, etc.), traffic source, and more information. So in just three button clicks, you can monitor your network traffic.
Setting up Zabbix to check the health of host machines requires more steps. A host can be a server or a network device. An agent you can download from the Zabbix site must be installed on each host to be monitored. From the same subcategory as ntop, you can select Zabbix Server Management to enter its configuration page. Before starting Zabbix, you must enable the mysqld and ntpd services, which you can do by clicking their respective buttons. After that, just start the Zabbix service, go to the Zabbix page to search for or add hosts, and you can start monitoring.
You can get a glimpse of your network’s security by starting Snort, located in WUI index under Security. Select the appropriate network interface; I selected the one connected before the firewall, since most attacks and intrusions come from the Internet. When I viewed the reports using Snort’s Acid interface, I saw a lot of alerts; if not for our firewall, our network could be down already.
I also tested the security of servers and workstations on our internal network using Nessus. I found positive vulnerabilities, but because NST doesn’t include a Nessus license, a more detailed report was not available.
Security at your fingertips
With its balanced set of network monitoring, analysis, and security applications, NST can give network administrators a much-needed selection of network monitoring and security for only the cost of an old server on which to run it. Through its WUI, which simplifies every process, network administrators who aren’t used to a Linux environment (especially the CLI) can easily utilize a comprehensive set of open source network tools. I plan to add this distribution to my personal toolkit for daily use.
Categories:
- Distributions
- Linux
- Security
- Reviews