Author: Cory Buford
pfSense is a free, powerful firewall and routing application that allows you to expand your network without compromising its security. Started in 2004 as a child project of m0n0wall — a security project that focuses on embedded systems — pfSense has had more than 1 million downloads and is used to protect networks of all sizes, from home offices to large enterprises. pfSense has an active development community, and more features are being added in each release to further improve its flexibility, scalability, and, of course, security.
The latest version, 1.2, includes features that you normally see on commercial firewall or router devices, including a Web-based GUI for easy management. While it has impressive features for a free firewall/router, it also suffers from some limitations.
As a firewall, pfSense supports filtering by source and destination address, by source and destination port, and by IP address. For example, if I use source address filtering and set the IP address to be monitored to be the subnet of the internal network, any traffic or request that originated from that address will be analyzed and filtered depending on the firewall rules. If I use destination filtering, the firewall will monitor the IP address that the traffic is going to, and if the destination address is within the firewall rules, then the appropriate action will be applied.
One of the best firewall features is its passive operating system fingerprinting (p0f) capability, which passively detects the connection’s OS and allows the firewall to block connections based on the connecting node’s OS. It also supports policy routing, and can operate in bridge or transparent mode, allowing you to just drop pfSense in between network devices without requiring additional configuration. pfSense provides network address translation (NAT) and port forwarding, but there are limitations with Point-to-Point Tunneling Protocol (PPTP), Generic Routing Encapsulation (GRE), and Session Initiation Protocol (SIP) when using NAT.
pfSense is based on FreeBSD, and FreeBSD’s Common Address Redundancy Protocol (CARP) provides redundancy by allowing administrators to group two or more firewalls into a failover group. Because it supports multiple wide area network (WAN) connections, it can perform outbound and inbound load balancing. The only limitation with this is that it can only do equal distribution of traffic between WAN connections, and you cannot prioritize specific traffic to be passed on a chosen connection.
pfSense supports virtual private networking (VPN) using Internet Protocol Security (IPSec), OpenVPN, or PPTP. Since there are some limitations with NAT, IPSec VPN is limited when connections are through NAT, resulting in a lack of support for remote or mobile VPN clients. The software also lacks advanced IPSec features like NAT Traversal in the Internet key exchange (IKE), known as NAT-T, and Xauth. You could choose OpenVPN to circumvent some of these limitations, but it too has some limitations, though the development team has promised to resolve these limitations in its next release. The pfSense site details the features and limitations.
Installing pfSense
To get started, download pfSense, and choose between an embedded package or a live CD ISO package. Choose the embedded package only if you’re going to use it on a compact network device that utilizes flash technology for storage. Most people should choose the live CD ISO for a normal PC. To run pfSense correctly, you need a box with at minimum a 100MHz CPU with 128MB of RAM and at least two network interface cards (NIC), one each for the WAN and LAN interfaces. This minimum requirement is good for a throughput of less than 10Mbps. As your network throughput and feature use increases, so too do the pfSense requirements. Check pfSense’s selection and sizing page to learn the most appropriate specifications for your requirements.
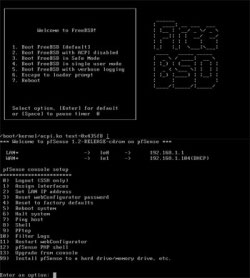
I downloaded the 60MB live CD ISO and burned it to a disc. Upon booting the live CD, you’re presented with several options. If this is your initial installation of pfSense, select the default option. The initial boot process consists of setting the VLAN and choosing the interfaces for LAN and WAN. You can automatically detect the interface settings, but make sure the interfaces are already connected. If they’re not, you’ll have to enter the interface names manually. For my setup, pfSense chose le0 for my LAN interface and le1 for the WAN.
After the initial configuration, the boot process continues until you reach pfSense’s console, which is a simple menu that lets you configure interface settings, activate Web configuration and other services, reset the configuration to factory defaults, and install pfSense to the hard disk. pfSense automatically assigns an IP address for the LAN interface, but I wanted to use a specific address, so I had to change the LAN IP address so that the new IP address would be used during the hard disk installation. I then proceeded to the straightforward hard disk installation.
You must format and create a disk partition before you install pfSense. If you choose the recommended partition, pfSense will create that for you. However, you still have the option to create you own partition layout. For my setup, I chose the default partition recommended by the installation. During the installation, pfSense asks you what type of system you want to install it on. You can choose a normal station (a uniprocessor or multiprocessor), a headless station without any console or keyboard, or an embedded system. I chose a uniprocessor system. After installation, restart your machine and, using the LAN IP address configure option, access the Web configuration interface.
Using pfSense
pfSense’s configuration is not too different from that of any network firewall and router that uses Web-based configuration. After you log in with the default username and password, you can configure the firewall’s interfaces and rules. For secure Web-based management, change the default password and set the session type to HTTPS on the general setup properties. Here you can also set the DNS settings of the firewall.
LAN configuration is straightforward. If you have not already done so before installing, you only need to set up the IP address. In the WAN interface, you can choose among various connections like Static, Dynamic Host Configuration Protocol (DHCP), Point-to-Point Protocol over Ethernet (PPPoE), and BigPond cable. Choose the appropriate connection as configured by your ISP.
Once you’ve configured the interfaces properly you can set up some firewall policies. As with any firewall device, setting up a firewall policy requires you to select an interface (WAN or LAN), source address and port, destination address and port, protocols and services, and pass, block, or reject action types. Block drops packets completely, while reject returns an “unreachable” response to the host initiating the connection. For security, it’s better to block than to reject. Under Firewall you can also configure NAT settings if you need to use port forwarding for services or configure static NAT (1:1) for specific hosts. NAT’s default setting for outbound connections is automatic/dynamic, but you can change that to manual if necessary. I tested some of the firewall rules I created, such as those for blocking FTP access to outside networks, and pfSense blocked the service successfully.
I also tested the VPN features of pfSense. It supports IPSec, OpenVPN, and PPTP. If you need a fast VPN connection and have less bandwidth available than is required by SSL VPN connections with good security, you can choose IPSec VPN. If you have handled IPSec VPN configuration in the past, you’ll find that configuring IPSec in VPN is a breeze and can be accomplished in just a few minutes. Make sure that the parameters for the algorithms in use are the same for both ends of the tunnel. Also note the limitations of IPSec VPN on the pfSense Developers Wiki. For simple IPSec configuration, pfSense’s limitations can be tolerated, and it works well for site-to-site setups that I’ve tested. However, for serious applications involving mobile clients and authentication, you’ll find the IPSec configuration in pfSense lacking.
You can use OpenVPN to circumvent IPSec’s limitations. Aside from that, OpenVPN can prove to be more secure, since it uses SSL. The only downside is that it requires more overhead due to the SSL, which also means that it eats more bandwidth than IPSec.
If you have VPN clients still using PPTP dial-up connections, pfSense fully supports PPTP as well.
Other features of pfSense, like its multiple WAN connection capability and its load balancing, are worth trying. You can also set up a “captive portal,” which requires every user who accesses the network to authenticate himself through a local database or Remote Authentication Dial-In User Service (RADIUS) before being allowed in. For users who need to access your network using PPPoE, a PPPoE server is available, and authentication may be based locally or via RADIUS.
Monitoring and logging events in pfTools is easy. It features real-time RRDtool graphs, visually displaying every operational process in your box, including traffic and system processes. Unlike some commercial network devices, the logs are well organized and can be located easily. This, along with included diagnostic tools like the traditional traceroute and a packet sniffer, proves to be helpful for efficient troubleshooting.
Does it make sense to try pfSense?
Although some features need improvement, pfSense’s capabilities as a firewall and router make it good enough to be put on an office network. It’s easy to manage and offers features that you see on commercial products. However, since some features commonly used in large enterprise networks are limited, I would not recommend it for such use. With its active development community, the project should resolve those issues as new features are added.
With its multiple WAN capability and load balancing, you can add pfSense to the growing list of low-cost, or free, network firewall/router solutions.
Categories:
- Networking
- Security
- System Administration
- Reviews