Author: Joseph R. Baxter
Corporations and home users alike need firewall protection. Many choices abound, including some expensive, commercial options that only run on specialized hardware. Others, like SmoothWall Express, are freely downloadable, built on the same technology as the commercial solutions, and even deliver some superior features.
SmoothWall Express 3.0, from August 2007, is an open source firewall distribution released under the GNU General Public License (GPL). It provides all the features commonly found in a modern system, but also a few that you might not expect. Stateful inspection, dynamic and static NAT, egress controls, demilitarized zone (DMZ) segmentation, and a Dynamic Host Configuration Protocol (DHCP) server are de rigueur in today’s world. However, this package adds a selection of proxy servers for the Web (content filtering is available in the commercial editions), POP3 mail, Session Initiation Protocol (SIP), Domain Name System (DNS), and instant messaging. You can configure the proxies to further protect networks with antivirus scanning and forensic logging, and Snort intrusion-detection software is built in for logging suspicious events. However, real-time alerting via email or SMS text messages is not available on the Express version. SmoothWall also features a simple quality of service (QoS) management that business and home users alike should find valuable.
With a free registered account, you can access my.SmoothWall, a hosted service that collects data on firewall specs, chipsets, and more. A world map plots the data, allowing you to anonymously view listings of hardware in use throughout the world. They have titled the beta my.SmoothWall Web site Firewall Management, but it is unclear how extensive this management will be in the final version. It might become a comprehensive set of tools like those that service providers on the SonicWALL platform use to administrate multiple customers; or it might remain only a place for update notifications and deployment data. In either case, this level of integration to the vendor Web site is almost unknown among open source firewalls.
On the down side, SmoothWall Express curtails the VPN features offered in commercial versions to simply provide support for an IPsec peer-to-peer endpoint. Authentication to common directories and databases (such as LDAP, AD, and NDS) is also available as value-added features. These design decisions tailor the product line to the user’s benefit — developer SmoothWall Limited maintains a revenue stream on enterprise-oriented technologies while still providing high-quality free software for branch VPNs, small businesses, and home users.
Installation
SmoothWall Express 3.0 is not an installable application but rather a full operating system and security appliance distribution. It requires a Pentium or better processor with at least 64MB of RAM for simple firewalling. In tests, a Pentium III with 512MB of RAM handled the load with all services started.
SmoothWall lives up to its name during the install process. You can download the fairly small image (69MB for the 32-bit version and 71MB for 64-bit), burn it to a CD, and install SmoothWall in just a few minutes. Should trouble arise, you can download comprehensive installation documentation.
Using the install CD was painless. Driver support seemed good, and the installer had no problem probing for common network cards. It even found a few oddball chipsets (Tulip-based) that had previously caused some confusion to one BSD-based firewall. The only hiccup came from an incompatibility with the LILO bootloader and one older AMD Athlon motherboard. LILO hung with a 02 error until I lowered the PIO Mode and UDMA settings on the IDE interface within the BIOS. Other systems I tested did not experience the issue.
During the install, before configuration begins, you must select one of three basic egress filtering settings: open, closed, or half-open. Open is precisely what it sounds like — essentially an Allow All setting to outgoing traffic. Closed is a Deny All to outgoing. Half-open is a prebuilt rule set that allows common protocols, such as HTTP/HTTPS, SMTP, POP3, FTP, and SSH, to leave the network, but denies all the rest. This setting is an effective compromise, and results in a safely functioning border device.
The software prompts to assign and configure the network interfaces, sets up the administrator password, then it reboots.
Configuration
After the install finishes, you do all further configuration via a browser. Each network card in a SmoothWall system is given a color designation. Green is for the internal segment, red denotes the connection to the Internet, and purple and orange designate DMZs for wireless access points or other Internet-facing servers. The interface is clean and well laid out, and works well with Mozilla Firefox, Google Chrome, and Microsoft Internet Explorer.
Since the install connected the red interface to the Internet, my first access of the home page led to the following message: There are updates available for your system. Please go to the “Updates” section for more information. I found the Updates menu item under Maintenance. Clicking Check for Updates yielded several results, but the update screen itself yielded no feedback other than the browser status bar. It gave no indication of whether a reboot was required after installing the updates. Yet after a reboot, the LILO menu contained a new option indicating an update had taken place. Some feedback to prompt a restart would have been appropriate. To its credit, however, the system performed a full reboot in less than a minute, even on less-than-optimal hardware.
While the out-of-the-box SmoothWall install works, additional customization brings out the real power of its features. The Services tab allows you to monitor each advanced feature, including time, remote access, intrusion detection, dynamic DNS updates, and proxy services. Each works flawlessly, although two strange elements seem contradictory. First, Secure Shell (SSH) access services and other services are not started by default, but ping (ICMP) is configured to reply both externally and internally. Second, while SmoothWall supports most dynamic DNS services, DNS-O-Matic is notably missing. An additional layer of Web filtering from OpenDNS via DNS-O-Matic would be a nice benefit. Still, unlike with many firewalls, you may use multiple dynamic DNS services simultaneously.
The Networking tab exposes the interface settings, IP address blocking, timed access, and traffic rules. Incoming and outgoing rules are easy to create and maintain. However, one idiosyncrasy results in behavior that is not obvious at first. Editing an outgoing rule actually removes it from the rule set completely. If you don’t add it back before navigating away from that page, it will be gone. Simply selecting a rule to view it in greater detail may inadvertently cause an administrator to break functionality to some application.
In the uncomplicated QoS configuration section, you can use drop-down boxes to select upload and download connection speeds and enable the service. The QoS engine prioritizes different types of traffic to make the connection speed seem faster. The settings are combo boxes, which makes them approachable even to non-technical users. By default, instant messaging traffic is set to low priority, VPN traffic to normal, and gaming traffic to high.
The Tools tab holds several useful utilities, such as ping and traceroute, as well as the Java-based SSH interface, which grants easy command-line access remotely. It extends the system beyond what the Web interface provides.
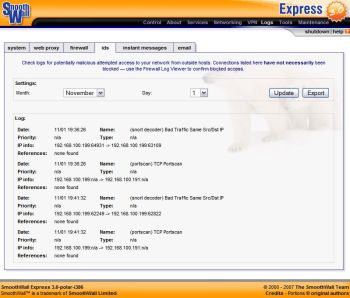
The Web interface features four other main tabs. The VPN configuration tab is limited in the Express edition, particularly in comparison to other firewalls in the SmoothWall family. As stated before, the Maintenance tab contains links to updates, passwords, and reboots. The About tab displays status for the system, bandwidth usage, and traffic monitoring in graphs accompanied by tabular data on all major services. Finally, the Logs tab lets you dive deeper into events. There you can find details about the system, Web proxy, firewall, IDS, instant messages, and email logs.
Although most logs are text-based listings, they include some advanced functionality. You can filter the Web proxy logs to ignore certain strings to pare down the results. The Firewall log not only displays a list of data, but it also provides the ability to look up a source or destination address directly from the log viewer. If an unwanted address appears, you can add it to the blocked IP list with the click of a button. The IM proxy, which logs conversations, works for most major services except Google Talk. The viewer contains a rich control that organizes conversations by service name (such as MSN and ICQ), by users in chat, and by date. The IM log widget refreshes periodically, which enables you to follow conversations in near real time.
The IDS log is not as feature-rich, but you can export most of the SmoothWall logs into CSV format from within the Web interface. You can then carry out forensic inspection of events elsewhere.
To test the firewall, I employed some tools found on the BackTrack live CD against the external (red) interface, and SmoothWall fared well. Network AutoScan found the SmoothWall firewall eventually, but the system appeared with a completely unknown fingerprint. At the same time within SmoothWall’s interface, the IDS log detected the scan as abnormal external traffic. Metasploit AutoPwn did not gain an attack surface and also generated logged port scans. On the internal network (green) interface, with ICMP turned off on the firewall, Nessus was helpless to discover that the host existed on the network.
Conclusion
SmoothWall provides robust features and usability, making it a good choice in spite of tough competition within its peer group. It makes complicated settings approachable and sets up filtering by default, which is considered advanced configuration in most other firewalls.
On the other hand, the distribution has a few issues and oversights. It could have better feedback within the interface, and there should be no doubt that an update is being applied or whether and when a reboot is required. Also, there should be no risk of accidentally deleting a firewall rule when an admin only wants to view a few details, and a correlation engine for the various logs would be useful. Simply being able to dredge all of the logs by a specific time frame would deliver a bigger-picture view for efficient investigation of suspected attacks.
Of course, no firewall is perfect or sufficient by itself. In-depth defense is the only strategy that has any hope of protecting valuable data and resources. SmoothWall Express 3.0 stands ready to occupy its place as a key part of that defense strategy for enterprise or home.
Categories:
- Reviews
- Security