Author: Federico Kereki
As important as security is, remaining current with every development is hard, and evaluating possible vulnerabilities across a network can be quite a chore. You need a way to both automate tests and make sure you’re running the most appropriate and up-to-date tests. Open Vulnerability Assessment System (OpenVAS) is a network security scanner that includes a central server and a graphical front end. The server allows you to run several different network vulnerability tests (NVT) written in Nessus Attack Scripting Language (NASL), which OpenVAS updates frequently.
OpenVAS is a fork of version 2.2 of the classic Nessus scanner. About three years ago, Nessus dropped the GPL, opting for a more commercial approach for its version 3.0. It decided to give away the software but charge for quick NVT upgrades and apply other restrictions. (Some restrictions were recently lifted for home users.) In July, OpenVAS came out with its 1.0 release and has made minor updates to it since then. All code is under the GPL.
Setting everything up
OpenVAS has a server/client architecture that comprises several components. On the server (Linux only), you need four packages:
- OpenVAS-Server: The basic scanning functionality
- OpenVAS-Plugins: A set of NVTs
- OpenVAS-LibNASL and OpenVAS-Libraries: Required for server functionality
On the client (Linux or Windows), you need only OpenVAS-Client.
Many distributions already include OpenVAS. I use openSUSE, and Smart as a package manager, and all I needed to do was install openvas-server openvas-manual openvas-plugins openvas-libraries openvas-client and everything was ready. Alternatively, you could visit the download site, get each package separately, and follow the included installation instructions.
After installing the packages, you need to perform several more steps as root on the server before you start the scans. First, use openvas-mkcert to create an appropriate certificate, so all communication between the server and clients can be encrypted. The certificate will have an expiration date, and eventually you will have to recreate it to continue using OpenVAS.
Next, open port 1241 on your firewall so clients can connect to the server. Then add users, specifying the login, authentication method (either a password or a certificate), and the access rules. Rules can be accept ip/mask (for example, accept 192.168.0.229/24) or deny ip/mask, and default accept or default deny. The first two rules specify which IP addresses you want OpenVAS to scan; a special client_ip parameter stands for whichever IP address the user logged in from. The latter two rules provide a default; if the user wants to scan an address that isn’t covered by the previous accept and deny rules, the default rule will apply. For example, having a single default accept rule means the user can scan every machine; the combination accept client_ip and default deny means the user can only scan his own box.
OpenVAS stores user configuration information under /var/lib/openvas/users/, with a directory for each user, so you can have different rules for each one. OpenVAS stores other server configuration items at /etc/openvas/openvasd.conf, though the standard, default values are probably good enough for you. The configuration file is appropriately commented, making changes easy.
Now the important part: running the tests. In order to test your security, you must have the most up-to-date NVTs. You should run openvas-nvt-sync frequently to update your local server tests. That utility uses rsync and md5sum, which you have to have installed on your own. Check the online documentation to add new NVT sources or certificates.
Once you’ve updated your NVTs you’re ready to start the server with the command openvasd -D. You can then start running tests from the clients.
Running tests
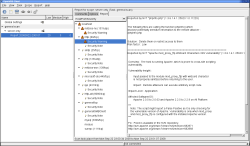
To run the client, execute OpenVAS-Client; be careful to use the uppercase letters. (In openSUSE, the client gets installed on the main menu under Utilities -> Security; that will vary for other distributions.) The main window is split into two sections: a treelist on the left has tasks, scopes, and reports, and several tabs on the right allow you to configure your scans. The first time you run the client, you will have only one entry on the left: Global Settings, with a default configuration. You must connect to a server to change the parameters.
To run a scan, you have to define a task. Click on the New Task icon on the toolbar, select an appropriate name for the task (such as Check Main Server), and describe it more fully in the Comments tab on the right.
Add a scope, which is just a complicated term meaning the whole configuration of the task. From the main menu, select Scope -> New. An empty scope will appear subordinated to your task, and an “unconnected” icon will appear next to the task name. Click on the “connect” icon on the toolbar, specify to which server you wish to connect, and enter your login name and password. You will get (at least the first time) some dialogs referring to the server certificate, and the client will download information on all possible NVTs from the server.
If you just want a fast, standard check after defining a task and its scope, click on Execute on the toolbar (or pick Scope -> Execute from the main menu), and OpenVAS will run all tests. When the job is done, a report entry will appear under your scope, giving details of the test. For each problem, you will get a Common Vulnerabilities and Exposures (CVE) number (like CVE-2008-1238); you can look up a full description on the CVE site or at the National Vulnerability Database. The report also gives some specific links as well as a proposed solution and an evaluation of the risk level (low, medium, or high) of any vulnerabilities it finds.
For more options, select the scope, and at the right you will be able to select, among other things:
- Which hosts to “attack”
- Which ports to check; you can choose either a comma-delimited list of ranges (25,80,1000-1023), -1 (meaning no checks), or the default (whatever you defined with global settings).
- How many hosts and how many checks will be run at the same time; a process is spawned for each host and check.
- Whether to run safe checks. If a check might cause a service to be disabled, then OpenVAS won’t perform the check. You can disable this option, at the risk of having OpenVAS disable a service.
- Which plugins to run, and options for them (though few have options). Plugins are grouped in families, and potentially unsafe checks are marked with an appropriate icon.
OpenVAS produces a report in HTML (including several graphics), LaTeX, or PDF (the latter only with the help of HTMLDOC, a non-free program).
Although Nessus has more available tests, OpenVAS’s own feed seems up to date. Give it a try before opting for a costlier, closed source program like Nessus.
Categories:
- Reviews
- Security