New Training Course Teaches Kubernetes Application Management with Helm
Oracle Linux 8 support with Oracle Enterprise Manager 13c release 13.4
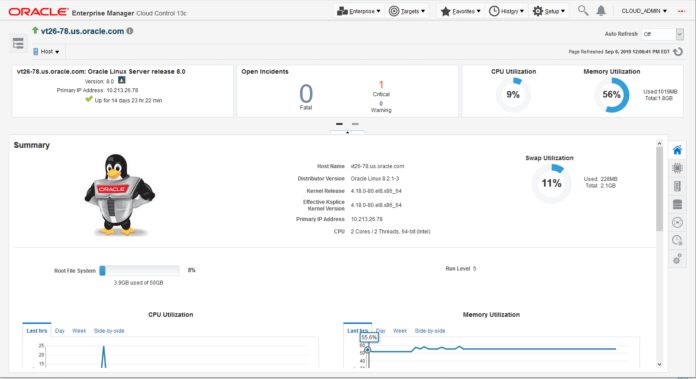
We are excited to announce support for Oracle Linux 8 within the Oracle Enterprise Manager 13c Oracle Linux Home portal and as a host target. This support is achieved with Release Update (RU) 4 of Oracle Enterprise Manager 13c release 13.4; for further details on RU4 please refer here. Certification for the Oracle Enterprise Manager OMS (Oracle Management Service) and Agent can be…
Click to Read More at Oracle Linux Kernel Development
Oracle Linux 8 support with Oracle Enterprise Manager 13c release 13.4
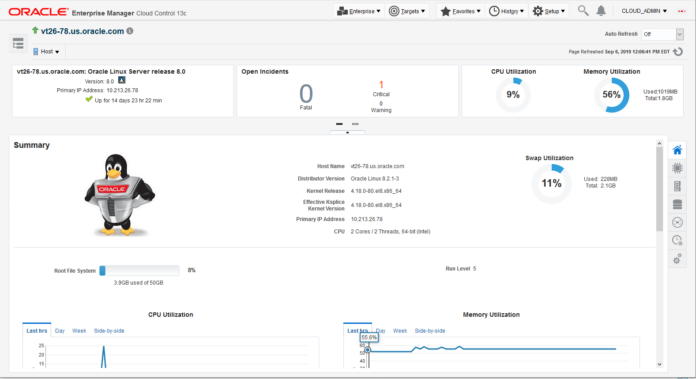
We are excited to announce support for Oracle Linux 8 within the Oracle Enterprise Manager 13c Oracle Linux Home portal and as a host target. This support is achieved with Release Update (RU) 4 of Oracle Enterprise Manager 13c release 13.4; for further details on RU4 please refer here. Certification for the Oracle Enterprise Manager OMS (Oracle Management Service) and Agent can be…
Click to Read More at Oracle Linux Kernel Development
Oracle Linux 8 support with Oracle Enterprise Manager 13c release 13.4
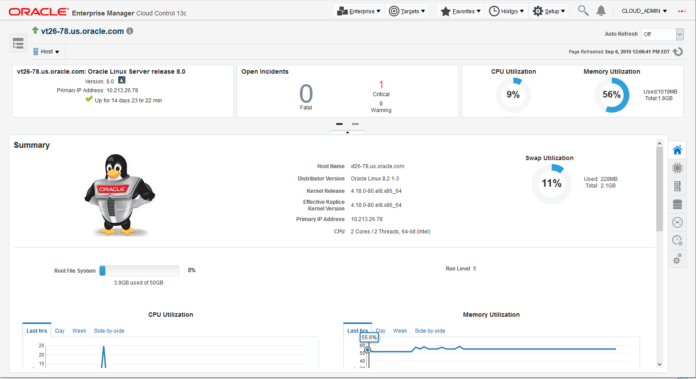
We are excited to announce support for Oracle Linux 8 within the Oracle Enterprise Manager 13c Oracle Linux Home portal and as a host target. This support is achieved with Release Update (RU) 4 of Oracle Enterprise Manager 13c release 13.4; for further details on RU4 please refer here. Certification for the Oracle Enterprise Manager OMS (Oracle Management Service) and Agent can be…
Click to Read More at Oracle Linux Kernel Development
New Kubernetes Security Specialist Certification to Help Professionals Demonstrate Expertise in Securing Container-Based Applications
The Linux Foundation’s First-Ever Virtual Open Source Summit (TechNewsWorld)
Jack M. Germain writes on Tech News World:
The success of The Linux Foundation’s first virtual summit may well have set the standard for new levels of open source participation.
Summit masters closed the virtual doors of the four-day joint gathering on July 2. The event hosted the Open Source Summit + Embedded Linux Conference North America 2020 and ended with more than 4,000 registrants from 109 countries.
The online platform InXpo enabled participants to be part of a real immersive technical gathering. They also can view on-demand content of sponsor resources and conference sessions for one year.
The InXpo platform enabled attendees to:
-
- View 250+ informative educational sessions and tutorials, across 14 different technology tracks, and participate in live Q&A;
- Join the ‘hallway track’ and collaborate via topic-based networking lounges in group chats, and connect with attendees in 1:1 chats;
- Visit the 3D virtual sponsor showcase and booths to speak directly with company representatives, view demos, download resources, view job openings and share contact info.
The summit’s virtual format also provided attendees the chance to “gamify” their event experience by earning points and winning prizes for attending sessions, visiting sponsor booths, and answering trivia questions.
Device Drivers Training Helps Advance an Embedded Linux Career
Anna-Lena wanted to improve her Linux kernel development skills, so she applied for and was awarded a Linux Foundation Training (LiFT) Scholarship in the Kernel Guru category.
Open Source Communities and Trademarks: A Reprise
The Linux Foundation has published a new blog about the use of Trademarks in open source communities:
A trademark is a word, phrase or design that denotes a “brand” that distinguishes one source of product or solution from another. The USPTO describes the usage of trademarks “to identify and distinguish the goods/services of one seller or provider from those of others, and to indicate the source of the goods/services.” Under US trademark law you are not able to effectively separate ownership of a project mark from control of the underlying open source project. While some may create elaborate structures around this, at the end of the day an important principle to follow is that the project community should be in control of what happens to their brand, the trademark they collectively built up as their brand in parallel with building up the functionality of their code.
For this reason, in communities that deem their brand important, we also file registrations for trademark protection to reserve the rights in the mark for the project, commonly in the United States, China, European Union, Japan, and other countries around the world. Registered marks will often have a ® symbol. This is different from a common law trademark right where you often see a ™ symbol with the mark. Having a registered trademark is often important because it enables us to better protect the community against misrepresentation, misuse, and confusion in the ecosystem between what is actually the community-built project, and what is not. This is often based on specific benefits that arise from the registration, which may vary from country to country.
Driving Compatibility with Code and Specifications through Conformance Trademark Programs
Scott Nicholas writes at the Linux Foundation blog:
A key goal of some open collaboration efforts — whether source code or specification oriented — is to prevent technical ‘drift’ away from a core set of functions or interfaces. Projects seek a means to communicate — and know — that if a downstream product or open source project is held out as compatible with the project’s deliverable, that product or component is, in fact, compatible. Such compatibility strengthens the ecosystem by providing end-users with confidence that data and solutions from one environment can work in another conformant environment with minimal friction. It also provides product and solution providers a stable set of known interfaces they can depend on for their commercially supported offerings.
A trademark conformance program, which is one supporting program that the LF offers its projects, can be used to encourage conformance with the project’s code base or interfaces. Anyone can use the open source project code however they want — subject to the applicable open source license — but if a downstream solution wants to describe itself as conformant using the project’s conformance trademark, it must meet the project’s definition of “conformant.” Some communities choose to use words other than “conformant” including “certified”, “ready”, or “powered by” in association with commercial uses of the open source codebase. This is the approach that some Linux Foundation projects take to maintain compatibility and reduce fragmentation of code and interfaces.
Understanding US export controls with open source projects
The Linux Foundation has produced a new whitepaper, in English and Chinese about export controls and open source and has summarized its findings on its blog:
The primary source of United States federal government restrictions on exports are the Export Administration Regulations or EAR. The EAR is published and updated regularly by the Bureau of Industry and Security (BIS) within the US Department of Commerce. The EAR applies to all items “subject to the EAR,” and may control the export, re-export, or transfer (in-country) of such items.
Under the EAR, the term “export” has a broad meaning. Exports can include not only the transfer of a physical product from inside the US to an external location but also other actions. The simple act of releasing technology to someone other than a US citizen or lawful permanent resident within the United States is deemed to be an export, as is making available software for electronic transmission that can be received by individuals outside the US.
This may seem alarming for open source communities, but the good news is open source technologies that are published and made publicly available to the world are not subject to the EAR. Therefore, open source remains one of the most accessible models for global collaboration.