As usual, last week’s Embedded World show in Nuremberg, Germany was primarily focused on commercial embedded single board computers (SBCs), computer-on-modules, and rugged industrial systems for the OEM market. Yet, we also saw a growing number of community-backed maker boards, which, like most of the commercial boards, run Linux. The new crop shows the growing diversity of hacker SBCs, which range from completely open source models to proprietary prototyping boards that nevertheless offer low prices and community services such as forums and open source Linux distributions.
The latest hacker SBCs include:
-
BeagleBone Blue — A robotics-focused spin of the BeagleBone Black
-
Chameleon96 — The first FPGA-enabled and first ARMv7 96Boards entry
-
NanoPi Neo2 — A headless, $15 boardlet that is the smallest quad-core ARMv8 SBC yet
-
Up Core — One of the smallest and most ARM-like x86-based hacker boards to date
In recent years, we’ve seen amazing price reductions and performance improvements on community-backed boards, as well as rampant imitation. The prime source of reflection is the Raspberry Pi, which recently spawned a wireless enabled, $10 Raspberry Pi Zero W. Cumulatively, the Raspberry Pi models are now said to be the third best-selling computer in history, beating out the Commodore 64 with 12.5 million units sold.
Because Raspberry Pi Trading has an exclusive deal with Broadcom on the boards’ BCM2836 and BCM2837 SoCs, there are no absolute clones of the RPi. However, the dimensions, the 40-pin expansion header, and in many cases the port layout and selection are imitated in dozens of SBCs.
None of the four boards covered here offer full RPi expansion compatibility, and they bravely head off in new directions. We’re seeing similar diversity in the latest COM/carrier board combinations. Nvidia’s third-generation, Linux-driven Jetson TX2 module launched earlier this month with a proprietary COM design, but with an open carrier board schematic, thereby enabling third-party participation.
Connect Tech responded with three carriers for the TX2, which features a high-end new Tegra Parker SoC designed for graphics and AI. These include a basic $99 Sprocket, a Spaceley board designed to work with Pixhawk drone autopilots, and a Cogswell carrier aimed at Gigabit Ethernet vision camera (GigE Vision) applications. Auvidea is also working on a carrier, and Connect Tech’s original three TX1-compatible carriers work on the TX2 as well as the TX1.
The new SBCs detailed below offer even more choices. Staking out new territory without RPi add-on compatibility is a risky choice, but so is introducing yet another me-too board that may struggle to differentiate. The following four Linux-friendly boards show some interesting new directions for hacker SBCs beyond DIY media players and home automation prototyping.
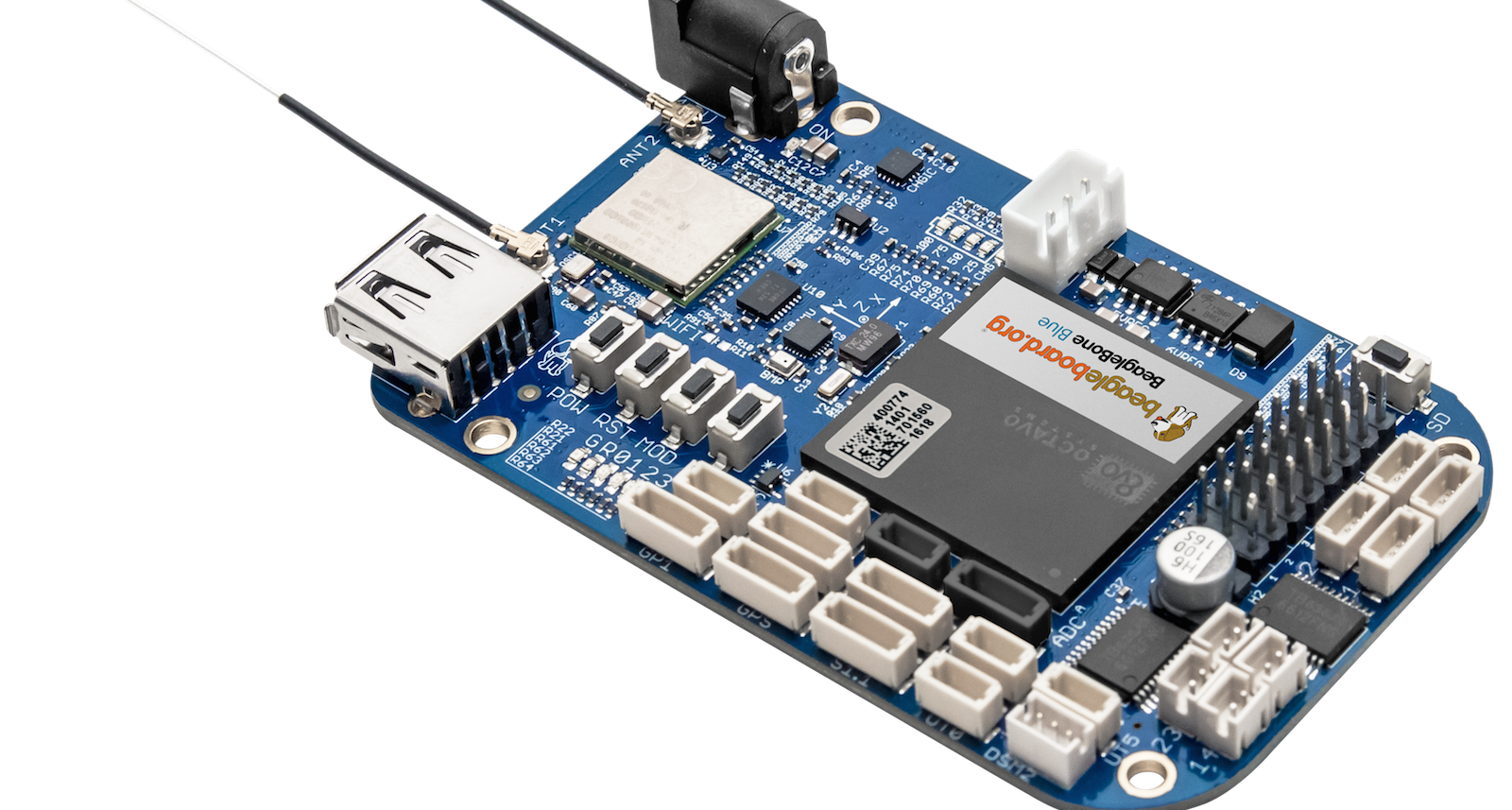
BeagleBone Blue
Over the past two years, BeagleBoard.org has worked with a variety of partners to produce certified pseudo-clones of the popular TI Sitara AM335x based BeagleBone Black. These include Seeed’s Grove compatible BeagleBone Green and BeagleBone Green Wireless and its own BeagleBone Black Wireless, which includes a SiP packaged core computer built by Octavo Systems. The new BeagleBone Blue is a robotics-focused collaboration with the University of California San Diego Robotics Lab, which is using the board for robotics education.
Like the BB Black Wireless, the $80 BeagleBone Blue has built-in wireless and an Octavo SiP package that pre-integrates the 1GHz, Cortex-A9 Sitara AM3358, 512MB RAM, and 4GB eMMC flash. The board also adds a battery connector, IMU, barometer, and motor control features like servos, encoder inputs, and motor outputs. While robotics has always been a strength of the BB Black, the BB Blue gives you most of the basic tools without requiring additional cape add-ons.
Chameleon96
Linaro’s open source 96Boards spec was adopted by some of the first 64-bit ARMv8 SBCs, including Arrow’s Qualcomm-backed DragonBoard 410C. Now Arrow has announced the first ARMv7 96Boards entry — and the first FPGA-enabled 96Boards SBC — with the Chameleon96. The SBC runs Debian Linux on a Cyclone V SE SoC from Intel PSG (Programmable Solutions Group), the new post-acquisition name for Intel’s Altera FPGA unit.
The Cyclone V combines dual 800MHz Cortex-A9 cores with a modest FPGA subsystem with 110K LE performance. Among other duties, the FPGA handles the video subsystem, which decodes and encodes 60fps 1080p streams via HDMI and MIPI-CSI interfaces, respectively. By applying FPGA to video, the board enables development of “custom IPU/GPU/VPU solutions,” says Arrow.
The Chameleon96, which like other 96Boards CE SBCs expresses most of its interfaces via 40-pin low- and 60-pin high-speed expansion connectors, is also notable for its integration of SecureRF’s quantum resistant cryptography technology. SecureRF’s Ironwood Key Agreement Protocol and Walnut DSA Digital Signature Algorithm are designed for securing reduced footprint, low-energy IoT devices.
NanoPi Neo2
The NanoPi Neo2 is the third iteration of the minimalist 40x40mm NanoPi Neo designs from FriendlyElec (FriendlyARM), following the NanoPi Neo and wireless-ready NanoPi Neo Air. The Ubuntu Core and Armbian Linux supported Neo2 advances to an ARMv8 quad-core, Cortex-A53 Allwinner H5, making it the world’s smallest 64-bit ARM hacker board. At $15, it’s also one of the most affordable.
The IoT-oriented NanoPi Neo2 is headless, without a real-world display port, so it’s not for your casual weekend hacker. The board offers 512MB of RAM, but storage is dependent on the microSD slot. Coastline ports include Gigabit Ethernet, USB 2.0 host, and micro-USB OTG. Onboard interfaces include an expansion interface that is said to be compatible with the first 24 pins of the Raspberry Pi.
UP Core
Unlike the above three boards, the UP Core is not a fully open source design, but Aaeon is otherwise striving to serve hobbyist makers as well as small-run commercial vendors. For example, the company has opened up the spec for its 100-pin expansion connector so third party developers can create their own boards that extend the SBC’s capabilities.
At 66×56.5mm, this community-backed board is smaller than the similarly quad-core Intel “Cherry Trail” Atom driven UP board. That’s only slightly petite by ARM standards, but the it’s one of the smallest x86 based hacker SBCs around. It will soon launch on Kickstarter for a price starting at $69. Once again, this is nothing special for ARM boards, but it’s cheap compared to most community-backed x86 SBCs.
The UP Core replaces the GbE port with WiFi and Bluetooth, but is otherwise a scaled back version of the original UP board. The SBC supports up to 4GB DDR3L RAM and up to 64GB eMMC, and coastline ports include HDMI and USB 3.0 ports. Additional interfaces include MIPI-CSI, USB 2.0, I2S, and eDP.
Aaeon’s parent company Asus has received even more attention for its quasi-open, maker-oriented Tinker Board. Launched in Europe in January, the $68 SBC runs Debian or Kodi on a quad-core Cortex-A17 Rockchip RK3288. The board features 2GB RAM, GbE, 4K video, and yes, that tried and true RPi-compatible 40-pin connector.
Connect with the Linux community at Open Source Summit North America on September 11-13. Linux.com readers can register now with the discount code, LINUXRD5, for 5% off the all-access attendee registration price. Register now to save over $300!