Home Search
applications - search results
If you're not happy with the results, please do another search
Best Practices for 2-Factor Authentication and Password Creation on Linux
As we mentioned in the previous article, web browsers present the largest and the most exposed attack surface on your Linux workstation. We’ve already...
Virtualization: The Smart-Connected Vehicle Enabler
The automotive electronic industry is now, more than ever, facing cybersecurity, connectivity, and software time-to-market challenges. Recently, in fact, vehicles have been hacked in...
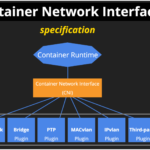
CNCF Hosts Container Networking Interface (CNI)
Today, the Cloud Native Computing Foundation (CNCF) Technical Oversight Committee (TOC) voted to accept CNI (Container Networking Interface) as the 10th hosted project alongside...
Web Developer Security Checklist
Developing secure, robust web applications in the cloud is hard, very hard. If you think it is easy, you are either a higher form of...
10 JavaScript Concepts Every Node.js Programmer Must Master
With JavaScript and the V8 engine at the core, an event-driven architecture, and scalability out of the box, Node.js has quickly become the new...
Using Docker in Production
Right now, Docker is an excellent tool to manage distributed applications. This is the result of quite a bit of evolution; in its earlier...
Product Development in the Age of Cloud Native
In a cloud native world, where workloads and infrastructure are all geared towards applications that spend their entire life cycle in a cloud environemnt,...
3 Benefits You Didn’t Expect from Linux Containers
Linux containers are gaining significant ground in the enterprise, which is not surprising, since they make so much sense in today’s business environment. With...
IBM’s OpenWhisk Stirs up Serverless IoT with Watson
With the Internet of Things, the realms of embedded Linux and enterprise computing are increasingly intertwined, and serverless computing is the latest enterprise development...
Creating Virtual Machines in KVM: Part 1
So, you want to stuff your Linux laptop or PC full of virtual machines and perform all manner of mad experiments. And so you...