Home Search
download - search results
If you're not happy with the results, please do another search
4 Best Practices for Web Browser Security on Your Linux Workstation
There is no question that the web browser will be the piece of software with the largest and the most exposed attack surface on...
Redefining the Tech that Powers Travel
We all know that the technology industry has been going through a period of incredible change. Rashesh Jethi, Head of Research & Development at...
Disruptive Collaboration: The Next Generation of Network Software and Hardware
About 10 years ago, mobile networks began experiencing massive increases in demand with the launch of the iPhone and the introduction of other smart...
Run Google Chrome on Raspberry Pi
Google Chrome is one of the most popular browsers all over the world. And Raspberry Pi is the most popular mini-PC device. But unfortunately,...
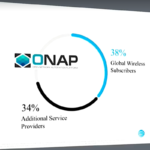
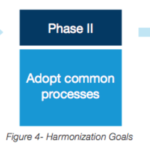
New Linux Foundation White Paper: Harmonizing Open Source and Standards in SDN
At the recent Open Networking Summit, the SDN/NFV community convened in Santa Clara to share, learn, collaborate, and network about one of the most...
Linux Kernel 4.11 Officially Released, Adds Support for Intel Gemini Lake SoCs
As expected, Linus Torvalds proudly announced today, April 30, 2017, the general availability of the final release of the Linux 4.11 kernel, a major update that...
Improve Your Online Security with Tails
The popular image of online dangers is scary bad guys trying to steal our stuff. This image is accurate if you remember to include...
How to Safely and Securely Back Up Your Linux Workstation
Even seasoned system administrators can overlook Linux workstation backups or do them in a haphazard, unsafe manner. At a minimum, you should set up encrypted...
Martin Casado at ONS: Making SDN Real
Software Defined Networking (SDN) has evolved significantly since the concept began to be considered in the 1990s, and Martin Casado, General Partner, Andreessen Horowitz,...
Keeping State and Networking in Kubernetes
In our previous installments of this series (see below), we learned a lot of neat things about Kubernetes. We learned that it is descended...