If you have high hopes of becoming a Linux administrator, there are plenty of tools you’ll need to know and know well. Some of those tools are limited to actions taken locally on the machine with which you are working: tools like iptables, make, top, diff, tail, and many more. These tools, isolated to the local machine, are invaluable to your task of managing those Linux servers and desktops. And even though GUI tools are available to help you with those tasks, understanding the command line is tantamount to understanding Linux.
But what about when you need to venture outside of 127.0.0.1 (aka, your local machine)? Administering a remote server cannot be accomplished with tools that do not contain the ability to reach beyond the local. That’s where the likes of ssh and scp come in handy. With these tools, you can easily work with remote machines to make your admin life considerably easier.
I want to introduce you to these two commands so that you can take advantage of what many would consider must-have Linux networking tools.
The need for more security
Secure Shell (otherwise known as ssh) is one of the first tools admins reach for when they must connect to a remote Linux server. By definition (from the ssh man page):
ssh (SSH client) is a program for logging into a remote machine and for executing commands on a remote machine. It is intended to provide secure encrypted communications between two untrusted hosts over an insecure network. X11 connections, arbitrary TCP ports and UNIX-domain sockets can also be forwarded over the secure channel.
The most important element of ssh is that of security. Where telnet and ftp allow you to do the same tasks as ssh and scp, they do so at the expense of security. If you value the precious information housed on your Linux machines, you full-well understand that telnet and ftp are to be shunned in favor of their more secure counterparts. With the likes of secure shell and secure copy, administrators can easily connect to their remote servers with an acceptable level of security.
So, how do we use these tools? Believe it or not, they are quite simple. Let’s start with the tool that will get your securely logged into your remote servers.
Ssh
The ssh command is quite simple to master. The format of the command looks like this:
ssh remote_host
where remote_host is either the IP address or URL of the remote server. The above command would work fine if you’re attempting to connect to a remote server with the same user being used on the local machine.
In other words, if I am on a local machine, logged in as olivia and I want to log onto olivia’s account on another Linux machine at 192.168.1.166, I can issue the command ssh 192.168.1.166. I would be prompted for the password associated with user olivia and, once I’ve authenticated, I will be presented with the bash prompt on the remote machine.
But what if I’m logged in on the local machine as nathan and need to connect to the remote machine as a olivia? Simple, I alter the command in the following way:
ssh -l olivia 192.168.1.166
That same action can be handled with a different form of the command, like so:
ssh olivia@192.168.1.166
Either way, I will be prompted for olivia’s password. Once authenticated, I will be logged into the remote machine as user olivia.
I prefer to have ssh output a bit more information as it makes a connection. For that, I employ the verbose option like so:
ssh -v -l olivia 192.168.1.166
When I do that, the ssh command will output information relative to making the connection (Figure 1).
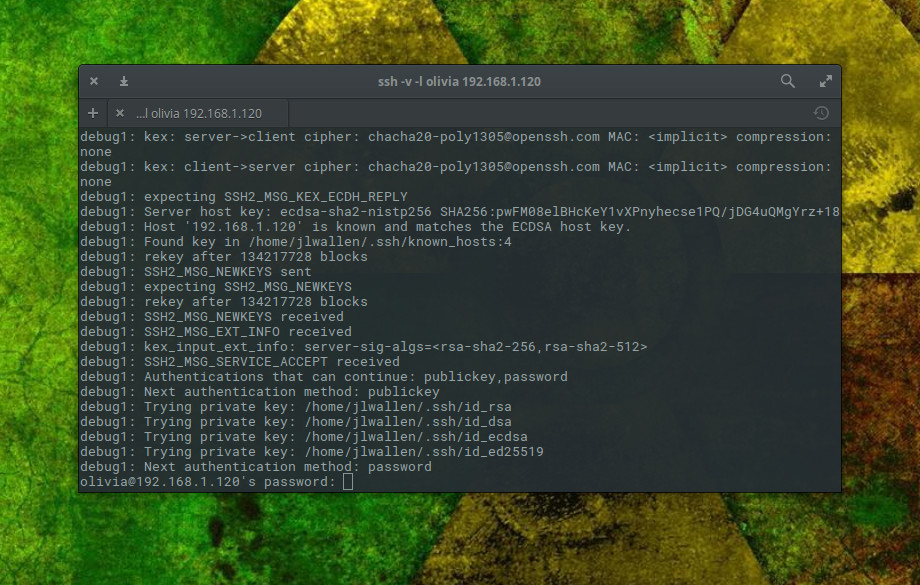
Secure Shell has several other tricks up its sleeve. One trick that many like to take advantage of is tunnelling X. This allows you to log into a remote machine and run the GUI tools from that machine on the local machine. Anything you do with that GUI tool will be reflected on the remote machine (not the local). To do this, you only have to add a simple switch like so:
ssh -l olivia -X 192.168.1.166
You can then issue a command to start a GUI application and have it run on the local machine (Figure 2).
What happens when you need to move files from a local machine to a remote machine? There’s a command for that.
Secure Copy
The secure shell command also happens to come with a protocol for handling the copying of files. Once upon a time, the standard tool for such a task was ftp. The ftp command is still heavily in use, but for those that prefer a much more secure method of transferring files, scp is what you want. With a structure similar to that of ssh, scp makes short work of moving files securely from one host to another.
With the scp command, you can send file to a remote host or copy them from a remote host. The syntax of the command can be a bit tricky, but once you understand it, it’s second nature.
Let’s first send a local file to a remote host. The structure of that command is:
scp filename username@remote_host:/some/remote/directory
Say we want to copy the file myfile to the Documents directory of remote user olivia on machine 192.168.166. Here’s how that command would look:
scp myfile olivia@192.168.1.166:/home/olivia/Documents
Enter olivia’s password, when prompted, and myfile will be securely copied to the directory /home/olivia/Documents/ on the machine at IP address 192.168.1.158.
Now, say you want to securely copy that same file from 192.168.1.158 into the Documents directory on the local machine. Do that, the command would now look like:
scp olivia@192.168.1.158:/home/olivia/Documents/myfile /home/olivia/Documents
You can now securely move files from one machine to another.
RTFM
As with any command, once you have the basics down, it is imperative that you (with a nod to Battlestar Galactica) Read The Frakking Manual (RTFM). For Secure Shell, issue the command man ssh and for Secure Copy, issue the command man scp. Both of these man pages will give you more information than you could possibly imagine about their respective commands.
If you’re looking for a secure route to working with remote machines, look no further than ssh and scp. Once you’ve mastered these two commands, you’ll be able to remotely (and securely) administer beyond the 127.0.0.1 address.
Advance your career in system administration! Check out the Essentials of System Administration course from The Linux Foundation.





