Tor is a software that enables you to hide your identity on the internet. It is an open network that helps defend against traffic analysis and grants you a high level of privacy.
Tor protects you by bouncing your communications around a distributed network of relays (known as onion routing) run by volunteers all around the world: it prevents somebody watching your Internet connection from learning what sites you visit, and it prevents the sites you visit from learning your physical location.
What is Onion Routing?
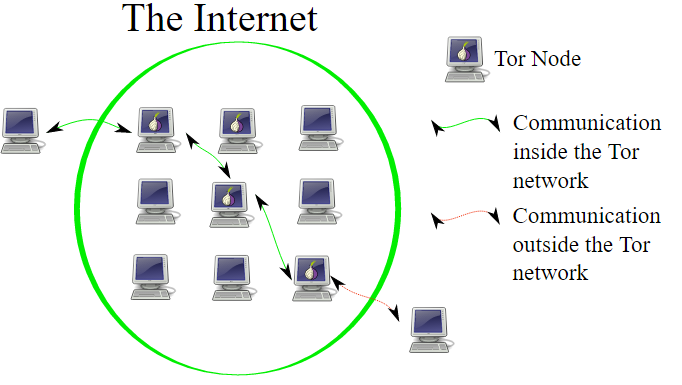
In onion routing, the data to be sent is encapsulated in layers of encryption, just like the layers of an onion. The resulting encrypted data is then transmitted through a series of network nodes called onion routers, each of which “peels” away (or decrypts) a single layer of the encryption, uncovering the data’s next destination. Upon decrypting the final layer, the data arrives at its destination. The sender remains anonymous because each intermediary knows only the location of the immediately preceding and following nodes.
How to Install Tor on Ubuntu
Follow these steps to install Tor on Ubuntu:
1. Adding Source Entries
First find out which version of Ubuntu you are using. Then choose that version from the following list and add the following lines to the file /etc/apt/sources.list using the editor you use or simply by using the cat command.
$ sudo cat >> /etc/apt/sources.list
- If you are using Ubuntu 14.xx
deb http://deb.torproject.org/torproject.org trusty main
deb-src http://deb.torproject.org/torproject.org trusty main
- If you are using Ubuntu 15.xx
deb http://deb.torproject.org/torproject.org wily main
deb-src http://deb.torproject.org/torproject.org wily main
- If you are using Ubuntu 16.xx
deb http://deb.torproject.org/torproject.org xenial main
deb-src http://deb.torproject.org/torproject.org xenial main
2. Adding GPG Key
Run the following commands in your terminal:
$ sudo gpg — keyserver keys.gnupg.net — recv 886DDD89
$ sudo gpg — export A3C4F0F979CAA22CDBA8F512EE8CBC9E886DDD89 | sudo apt-key add -
3. Installing Tor
Now run these commands to install Tor.
$ sudo apt-get update
$ sudo apt-get install tor deb.torproject.org-keyring
Using Tor
1. Configuring Tor
Tor puts the torrc file in /usr/local/etc/tor/torrc if you compiled tor from source, and /etc/tor/torrc or/etc/torrc if you installed a pre-built package.
Tor comes with a control port, which can be used to control it. It is highly recommended that in order to control Tor using the control port, you set up an authentication method to prevent anyone else from accessing it. The recommended way is to use a password. If you choose to use a password for authentication first run this command to get a hashed password to use in the config file in the next step:
$ tor --hash-password "passwordhere"
16:AC5FB526B90B4ED06027C6C4343EF87075B63B9A25822EE198622EE4D6
Open the torrc file (if you followed the above installation steps, then your torrc file path should be /etc/tor/torrc) and uncomment these lines:
- ControlPort
- CookieAuthentication OR HashedControlPassword (if you choose to uncomment HashedControlPassword, copy the hashed password you got in the previous step and paste it next to HashedControlPassword in the torrc file)
These lines are shown below:
# This provides a port for our script to talk with. If you set this then be
# sure to also set either CookieAuthentication *or* HashedControlPassword!
#
# You could also use ControlSocket instead of ControlPort, which provides a
# file based socket. You don't need to have authentication if you use
# ControlSocket. For this example however we'll use a port.
ControlPort 9051 # <--- uncomment this ControlPort line
# Setting this will make Tor write an authentication cookie. Anything with
# permission to read this file can connect to Tor. If you're going to run
# your script with the same user or permission group as Tor then this is the
# easiest method of authentication to use.
CookieAuthentication 1 #either uncomment this or below HashedControlPassword line
# Alternatively we can authenticate with a password. To set a password first
# get its hash...
#
# % tor --hash-password "my_password"
# 16:E600ADC1B52C80BB6022A0E999A7734571A451EB6AE50FED489B72E3DF
#
# ... and use that for the HashedControlPassword in your torrc.
HashedControlPassword 16:E600ADC1B52C80BB6022A0E999A7734571A451EB6AE50FED489B72E3DF #if you choose to uncomment this line, paste your hashed password here
Cookie authentication simply means that your credential is the content of a file in Tor’s DataDirectory.
In order for the changes to take effect, you must restart Tor using this command:
$ sudo /etc/init.d/tor restart
2. How to authenticate with Tor Control Port
If you want to authenticate with Tor to communicate with the Tor control port (e.g. to start a new session), you can do this: (if you chose cookie authentication method, you can use AUTHENTICATE without any password)
$ echo -e 'AUTHENTICATE "passwordhere"rnsignal NEWNYMrnQUIT' | nc 127.0.0.1 9051
By default, Tor listens for SOCKS connections on port 9050. To use this SOCKS proxy, you can point your application directly to it (“localhost” port “9050”). For applications that do not have this feature, you can use torsocks.
3. How to install torsocks
To install torsocks you can either directly run this command:
$ sudo apt-get install torsocks
ALTERNATIVELY, To install it directly from source (this gets you the latest version and recent patches):
$ git clone https://git.torproject.org/torsocks.git
$ cd torsocks
$ ./autogen.sh
$ ./configure
$ make
$ sudo make install
Now let’s use torsocks! First, get your public ip address.
$ curl 'https://api.ipify.org'
75.119.16.140
So, it says 75.119.16.140 is my public ip, now use torsocks before the curl command:
$ torsocks curl 'https://api.ipify.org'
31.45.26.14
As you can see, we now have a different ip address that was used to browse on the internet.
4. Signalling Tor Control to create a new circuit (or path)
You can tell Tor control to initiate a new Tor circuit. An important thing to note here is that a new circuit does not necessarily mean a new IP address. To do this, we use a command already introduced above:
$ echo -e 'AUTHENTICATE "passwordhere"rnsignal NEWNYMrnQUIT' | nc 127.0.0.1 9051
ALTERNATIVELY, if you want to use telnet:
$ telnet localhost 9051
Trying 127.0.0.1...
Connected to localhost.
Escape character is '^]'.
AUTHENTICATE "my_password"
250 OK
SIGNAL NEWNYM
250 OK
QUIT
250 closing connection
Connection closed by foreign host.
5. Use a Python Controller Library for Tor
Stem is an officially supported Python controller library for Tor. You can find all about how to install Stem and a few good tutorials to start with from the official website of Tor.
This article was contributed by a student at Holberton School





