Much of Mozilla’s engineering effort goes into direct enhancement of the contemporary Web-browsing and email experience: Firefox and Thunderbird, standards support, new APIs, etc. But some of its value is indirect, such as the Mozilla Watchdog initiative, which aims to better equip Web users to protect themselves against fraud. The Watchdog tools help you protect your passwords and make you more aware of threats to your security – which is certainly valuable for individuals, and even more so for organizations.
Watchdog was launched in late 2011, with the stated goal of “nudging” users to “to make better, more informed password and privacy decisions.”
The initial announcement cited a handful of scenarios where the browser could assist the user: raising the user’s attention when using the same password on too many sites, helping to point out privacy options, and automating important steps that are easy to overlook.
Visual feedback for passwords
The first code arrived in December, in the form of the Visual Hashing extension.
Although a Mozilla effort, the extension was also released for Google’s Chrome. (Update: An extension for Chrome has not been released. Apologies for the error.) In either browser, the extension provides visual feedback cues to the user on all HTML password fields. As you type, the contents of the text entered are hashed and the result is translated into four HTML color-codes, which are overlayed on the background of the field. The result is that you get a subtle reminder of your password.
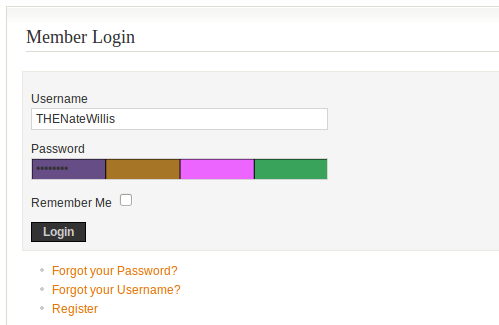 The theory at work here is that the color bars provide an easy to recognize form of feedback as you type, to make password memorization easier — without resorting to “Show Passwords” or another method. Plus, the color code changes as you type, which means that instead of associating each password with a fixed “color bar-code” (so to speak), your brain learns to associate a pattern of colors with the correct keystrokes.
The theory at work here is that the color bars provide an easy to recognize form of feedback as you type, to make password memorization easier — without resorting to “Show Passwords” or another method. Plus, the color code changes as you type, which means that instead of associating each password with a fixed “color bar-code” (so to speak), your brain learns to associate a pattern of colors with the correct keystrokes.
Because the hashing algorithm used (SHA-1) maps keystrokes to pseudorandom, well-distributed values, typing even one character wrong radically changes the output. Over time, you learn to recognize the multi-color feedback, so your typos immediately stand out, before you hit “Submit” and potentially send the wrong password to server. It is easy to think that the color feedback won’t be useful, but you would be surprised. I was also a big fan of the now-defunct ChromaTabs extension, which hashed base URLs to tint the background of Firefox tabs, and it is amazing how quickly your brain connects the color with proper input.
The pseudorandomness of SHA-1’s color hashes also ensures that extension is effective for the vast majority of users with some form of color-deficient vision, although obviously someone complete monochromatic vision will not see the benefits.
Finally, for the security conscious, the extension does “salt” the hash function, which introduces an imperceptible adjustment to the color codes, so that no one can take a screenshot and reverse-engineer a password by examining the color bars.
Password Re-Use
While visual feedback is a training system to make users more consciously aware of their passwords, the second Watchdog offering, Password Reuse Visualizer, is more of an educational tool. Also available for both Firefox and Chrome, it won’t affect your day-to-day browsing, but by sitting down and firing it up, you will hopefully start to take a more serious approach to password overuse.
The problem is that passwords are hard to come up with, at least if you want them to be both memorable and strongly unguessable. The natural inclination is to reuse a small set of “good” passwords over a variety of sites. While that works fine for unimportant sites, without discipline you can develop the bad habit of using the same password both for a sensitive service (perhaps with good HTTPS support) and for one run by a sloppy administrator that leaks data.
The Password Reuse Visualizer lets you see how bad your own habits have gotten courtesy of a graph that connects one node for each saved password to dots for every site where it is used. See a giant cluster developing around one node, and you have a reuse problem. The passwords graphed by the extension are only those saved by the browser, so they may or may not give you a full picture, but then again this is primarily a tool for taking stock of your current situation. The actual passwords are displayed using the four-color-barcode technique from the Visual Hashing extension, although you can click through to see them in the clear as well.
Similar-but-not-identical password nodes are connected by links of a different color (as well as by a square instead of a circle). Whether or not groupings of similar passwords represent a security problem is more debatable; in practice it depends on the sites and the passwords, although “password families” are always a better approach than simple re-use.
Although taking stock of your password reuse is a good idea, the extension does not help you take steps to fix any overuse problems, nor does it (for example) alert you when choosing a new password if you are going to the same well yet again. It is possible that we will see Mozilla Watchdog offer more proactive measures in the future (including reports of a secure password-generator), but for right now, the educational value of the work is important enough to recommend on its own merits.
New Ideas in Privacy and Security
Of course, another approach to the password-juggling problem is to punt and only use third-party authentication services like OAuth. Mozilla regards OAuth as a privacy risk, however, due to the fact that so many brokers are commercial companies out to monetize account info for advertising. OpenID leaves the user in control, but it is agonizingly convoluted and adoption has been slow.
Mozilla has its own solution in the works, called BrowserID. We covered the project’s launch in July 2011. The mechanism basically allows you to sign-in to a Web site using a system most users are already comfortable with: email verification. It is quick, as secure as one’s email account, and not difficult to understand. But BrowserID had a significant problem: it only worked when the browserid.org server “vouched” for an address.
That has now changed, and email providers can directly authenticate an identity to any BrowserID-consuming site. We are still waiting on major email providers to announce support for the protocol (and with some of them, it could be a long wait), but the change represents the removal of an important technical hurdle. As the BrowserID blog notes, direct email-provider-vouching cuts down the number of steps in the process by seven. There is no predicting how well BrowserID will catch on, but there is at least a case to be made that it offers an easier-to-understand — and thus easier to secure — alternative to other protocols.
There is no doubt that, taken individually, the projects mentioned here do not solve persistent security or privacy problems. But all too often in security matters, we can let the perfect be the enemy of the good. Mozilla Watchdog offers simple tools, but they can play an important role in educating users about online password and browsing security — a topic where the easiest attacks to prevent are well-understood.





