Sysadmins are increasingly looking to expand their skillsets and carve out new opportunities. With that in mind, many sysadmins are looking to the world of DevOps. At lots of organizations, DevOps has emerged as the most effective method for application delivery, including in the cloud.
One of the drivers of the DevOps movement is that organizations simply have limits on the number of IT staffers, sysadmins, and developers that they can employ. Cross-pollination of traditional skillsets makes good business sense. And, as Jeff Cogswell has noted, “The line between hardware and software is more blurry than it used to be.”
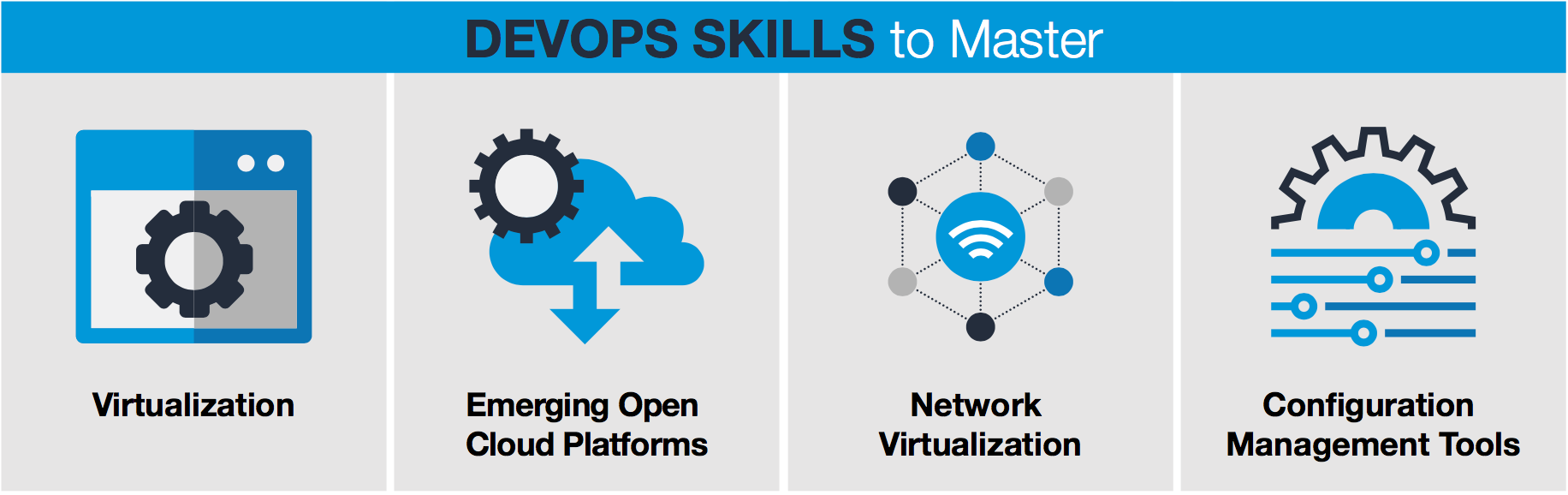
Cogswell also laid out a good recipe for what specific skills to master in order to meet DevOps goals:
-
Learn what virtualization is and how, through software alone, you can provision a virtual computer and install an operating system and a software stack.
-
Study emerging open source platforms and frameworks, such as OpenStack.
-
Learn network virtualization.
-
Learn to use configuration management tools, such as Puppet and Chef.
All of these pursuits can help sysadmins appeal to organizations looking to create more collaborative and efficient working environments. Additionally, as mentioned earlier, fluency and facility with emerging cloud, virtualization, and configuration management tools can make a substantial compensation difference for sysadmins.
Training options
Sysadmins interested in becoming more fluent with DevOps skills and practices can start by exploring Dice’s Skills Center. A look there makes it clear that skillsets surrounding configuration management tools, containers, and open platforms are much in demand. Savvy sysadmins can combine existing competencies with these skillsets and move the needle.
Flexible training options are available for these tools. For example, if you just want to take Puppet for a test drive within a virtual machine, you can do so here, or there are instructor-led and online training options detailed on the same page. For example, you can chart a learning roadmap for Puppet, find in-person or online training options for Chef, or sample some of the available online tutorials.
A great way to learn more about cloud skills is to open an account on Amazon Web Services and work with EC2 technology. OpenStack training options also abound. The Linux Foundation, for example, offers an OpenStack Administration Fundamentals course, which serves as preparation for certification. The course is available bundled with the COA exam, enabling students to learn the skills they need to work as an OpenStack-skilled administrator and get the certification to prove it.
The Guide to the Open Cloud 2016 from The Linux Foundation also includes a comprehensive look at other cloud platforms and tools that many sysadmins would be wise to pick up. Mirantis and other vendors, such as Red Hat, also offer certified OpenStack administrator curriculum.
Finally, scripting and development skills can also expand a sysadmin’s horizons and fit in with organizational DevOps goals. Scripting skills, from Python to Perl, are a valuable part of sysadmin’s toolkit. The Linux Foundation offers coursework in this area, too, including Developing Applications for Linux and Linux Performance Tuning. Additionally, The Foundation offers an Introduction to DevOps course that is worth exploring.
In the next article, we will explore specific professional certifications and relevant training to help you move to the next level.
Learn more about essential sysadmin skills: Download the Future Proof Your SysAdmin Career ebook now.
Read more:
Future Proof Your SysAdmin Career: An Introduction to Essential Skills
Future Proof Your SysAdmin Career: New Networking Essentials
Future Proof Your SysAdmin Career: Locking Down Security
Future Proof Your SysAdmin Career: Looking to the Cloud
Future Proof Your SysAdmin Career: Configuration and Automation