Last year, experts from Uber, Twitter, PayPal, and Hubspot, and many other companies shared how they use Apache Mesos at MesosCon events in North America and Europe. Their talks helped inspire developers to get involved in the project, try out an installation, stay informed on project updates, and generally get pumped to use and participate in Apache Mesos.
The MesosCon program committee is now seeking proposals from speakers with fresh ideas, enlightening case studies, best practices, or deep technical knowledge to share with the Apache Mesos community again this year. MesosCon is an annual conference held in three locations around the globe and organized by the Apache Mesos community in partnership with The Linux Foundation.
March 25 is the deadline for speakers to submit proposals for MesosCon Asia. MesosCon North America’s deadline is May 20 and MesosCon Europe’s is July 8. Here, we’ve rounded up the top 5 videos from the 2016 MesosCon North America event for some inspiration. Submit your speaking proposal now!
1. How Verizon Labs Built a 600 Node Bare Metal Mesos Cluster in Two Weeks
Craig Neth, Distinguished Member of the Technical Staff at Verizon Labs, describes building a 600-node Mesos cluster from bare metal in two weeks. His team didn’t really get it all done in two weeks, but it’s a fascinating peek at some ingenious methods for accelerating the installation and provisioning of the bare hardware, and some advanced ideas on hardware and rack architectures.
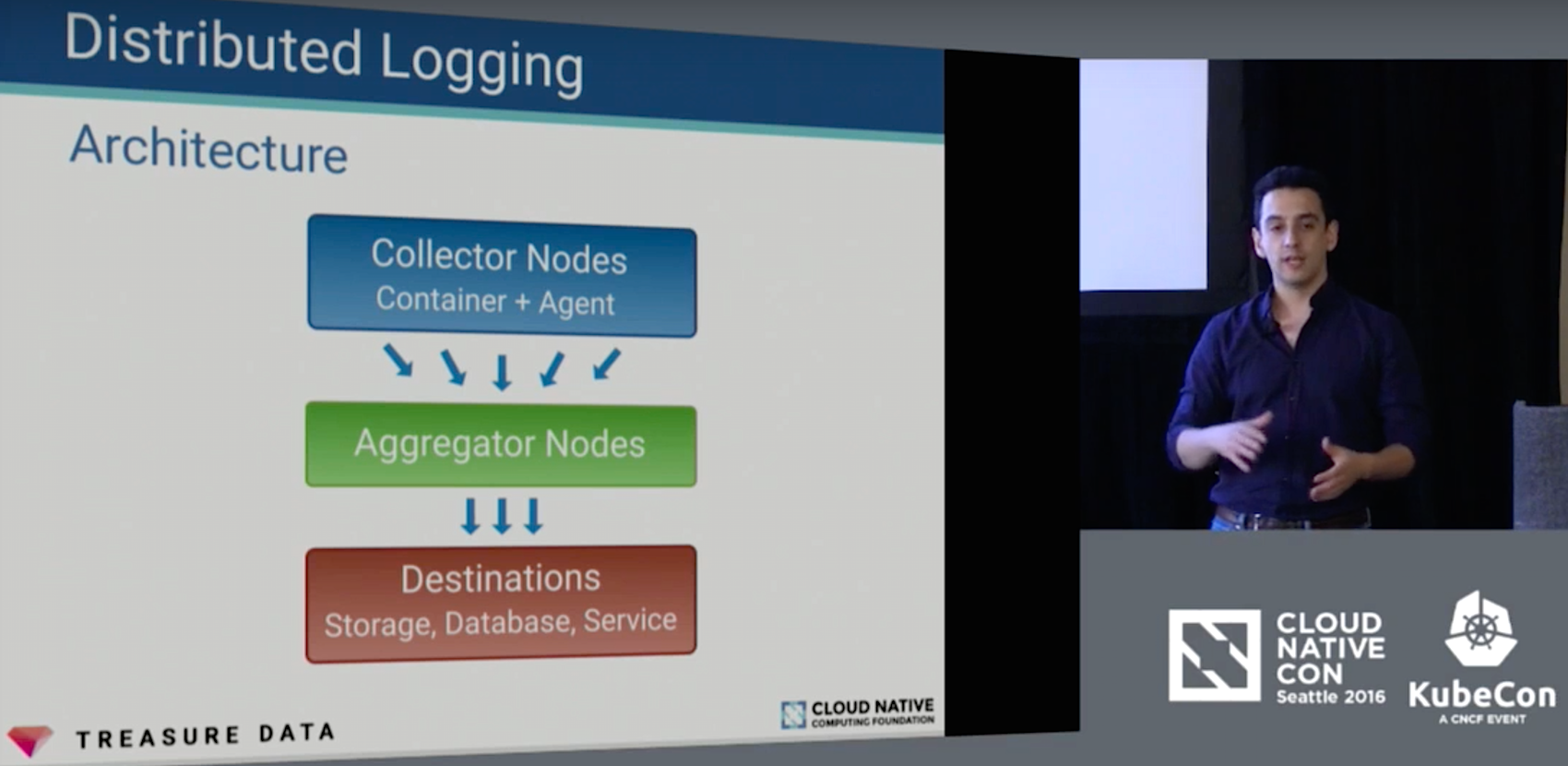
2. 4 Unique Ways Uber, Twitter, PayPal, and Hubspot Use Apache Mesos
Dr. Abhishek Verma, first author of the Google Borg Paper, describes how Uber used the Apache Cassandra database and Apache Mesos to build a fluid, efficient cluster of geographically diverse datacenters. The goals of this project were five nines reliability, low cost, and reducing hardware requirements. Mesos allows such flexible resource management that you can co-locate services on the same machine.
3. Apache Mesos for Beginners: 3 Videos to Help You Get Started
“How do I get my hands on this? I don’t have a datacenter or a team of engineers. What if I want to become a contributor? How do I make this all go in my own little test lab?”
The talks highlighted in this article will help you answer these questions. Aaron Williams, Joris Van Remoorter, and Michael Park of Mesosphere, and Frank Scholten of Container Solutions share how to run Mesos on a laptop, how to become a contributor, and the basic architecture of a Mesos-based datacenter.
4. Apache Spark Creator Matei Zaharia Describes Structured Streaming in Spark 2.0
Apache Spark has been an integral part of Mesos from its inception. Spark is one of the most widely used big data processing systems for clusters. Matei Zaharia, the CTO of Databricks and creator of Spark, talked about Spark’s advanced data analysis power and new features in its upcoming 2.0 release in his MesosCon 2016 keynote.
5. Open Source Is Key to the Modern Data Center, Says EMC’s Joshua Bernstein
DevOps is key to agility, agility is key to innovation and success, and open source powers DevOps. Joshua Bernstein, Vice President of Technology at EMC, describes the value that this brings to an organization: “We automate everything. We drive out corner cases. We strive for commodity hardware…The biggest thing is that we value this ability to interoperate. This goes along with microservices and the way that we build microservice applications now. We also value tremendously the ability to leverage a collaborative community.”
Submit a proposal to speak at MesosCon Asia » The deadline is March 25.
Submit a proposal to speak at MesosCon North America » The deadline is May 20.
Submit a proposal to speak at MesosCon Europe » The deadline is July 8.
Not interested in speaking but want to attend? Linux.com readers receive 5% off the “attendee” registration with code LINUXRD5.
Register for MesosCon Asia » Save $125 through April 30.
Register for MesosCon North America » Save $200 through July 2.
Register for MesosCon Europe » Save $200 through August 27.
Apache, Apache Mesos, and Mesos are either registered trademarks or trademarks of the Apache Software Foundation (ASF) in the United States and/or other countries. MesosCon is run in partnership with the ASF.