Home Search
bit - search results
If you're not happy with the results, please do another search
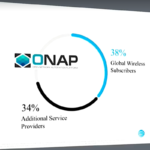
Disruptive Collaboration: The Next Generation of Network Software and Hardware
About 10 years ago, mobile networks began experiencing massive increases in demand with the launch of the iPhone and the introduction of other smart...
Join The Linux Foundation at OSCON for Booth Swag, Project Updates, and More
Going to OSCON on May 10-11 in Austin? While you’re there, be sure stop by The Linux Foundation training booth for fun giveaways and a...
Pros and Cons of System Update and Integrity Protection Schemes
Given the increasing malware attacks against Linux-based IoT devices, there is growing interest in integrity protection schemes, as well as system update mechanisms that...
New Strain of Linux Malware Could Get Serious
A new strain of malware targeting Linux systems, dubbed "Linux/Shishiga," could morph into a dangerous security threat.
Eset on Tuesday disclosed the threat, which represents a...
How to Safely and Securely Back Up Your Linux Workstation
Even seasoned system administrators can overlook Linux workstation backups or do them in a haphazard, unsafe manner. At a minimum, you should set up encrypted...
Martin Casado at ONS: Making SDN Real
Software Defined Networking (SDN) has evolved significantly since the concept began to be considered in the 1990s, and Martin Casado, General Partner, Andreessen Horowitz,...
Getting to Know GNOME (From a Unity Perspective)
Unless you’ve lost all network connections over the past couple of weeks, you know the big news: Canonical announced it was dropping Ubuntu Unity...
Building a Wearable Device with Zephyr
The Linux Foundation’s open source Zephyr Project received considerable attention at this February’s Embedded Linux Conference (ELC). Although there are still no shipping products...
Probe Your Linux Sockets With ss
We all know and love netstat (network statistics), because it is a wonderful tool for viewing detailed network connection information. An interesting alternative is...
Blockchain’s Weak Spots Pose a Hidden Danger to Users
Technologists, entrepreneurs, and some big companies are busy dreaming up new ways of using the core of Bitcoin—a distributed cryptographic ledger, or blockchain—to reinvent...