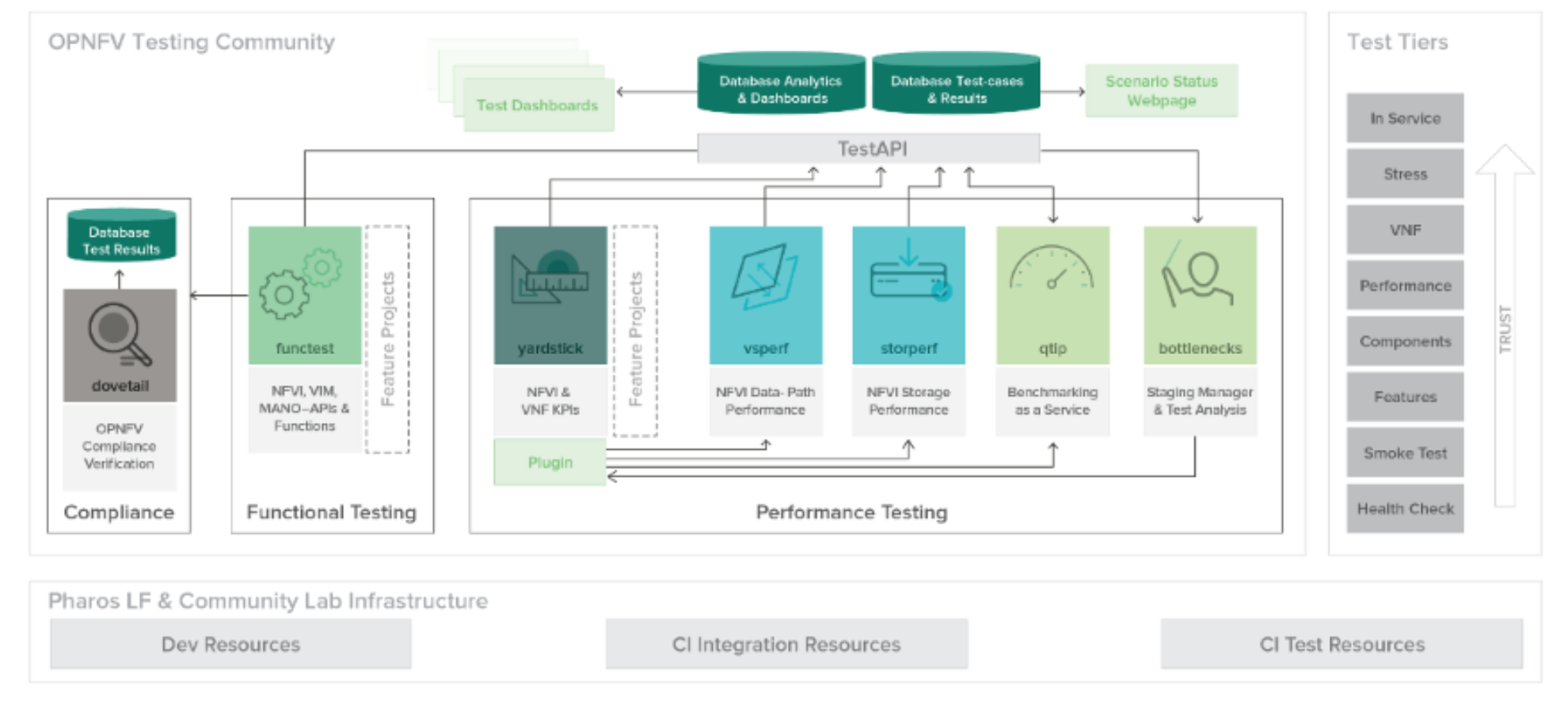
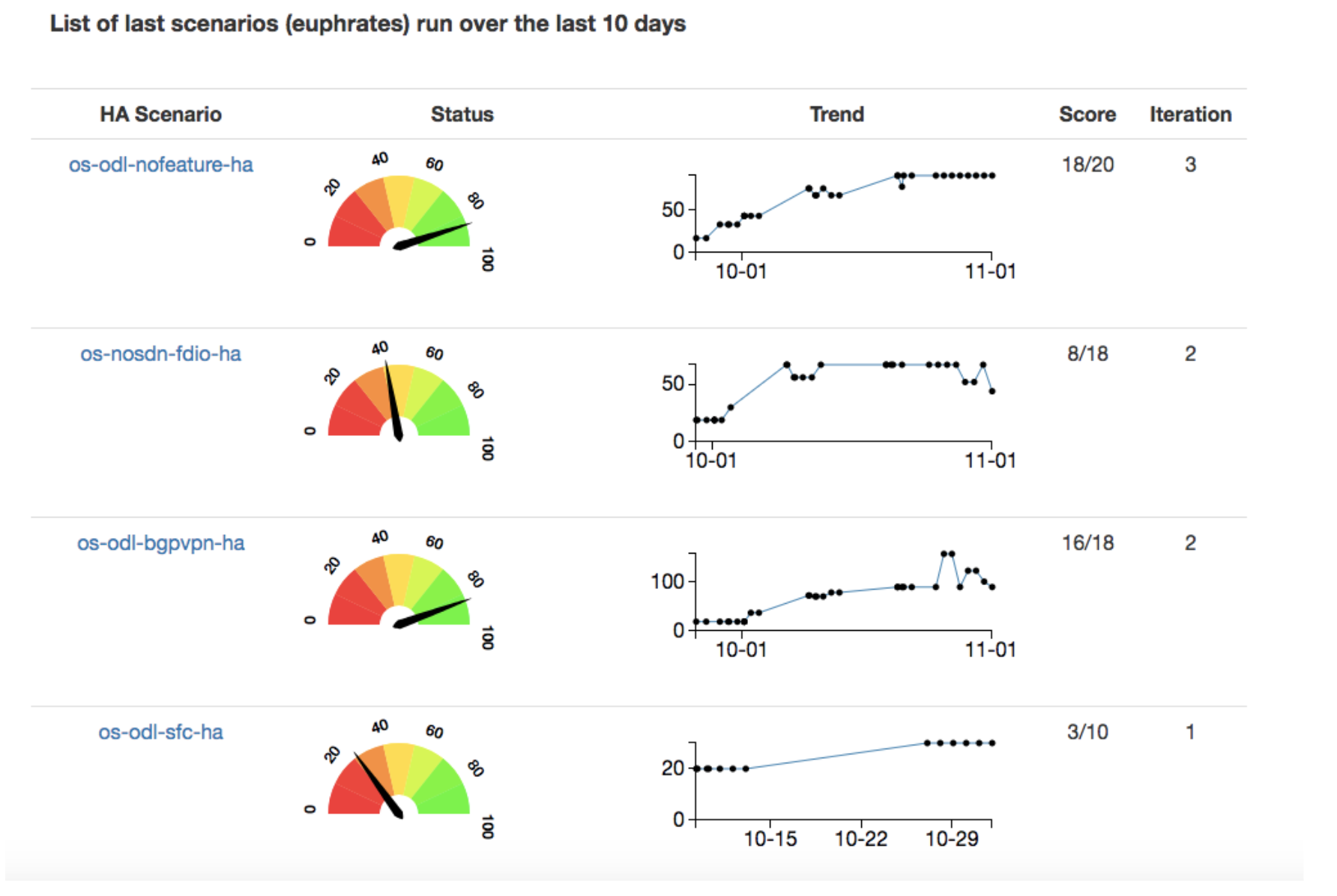
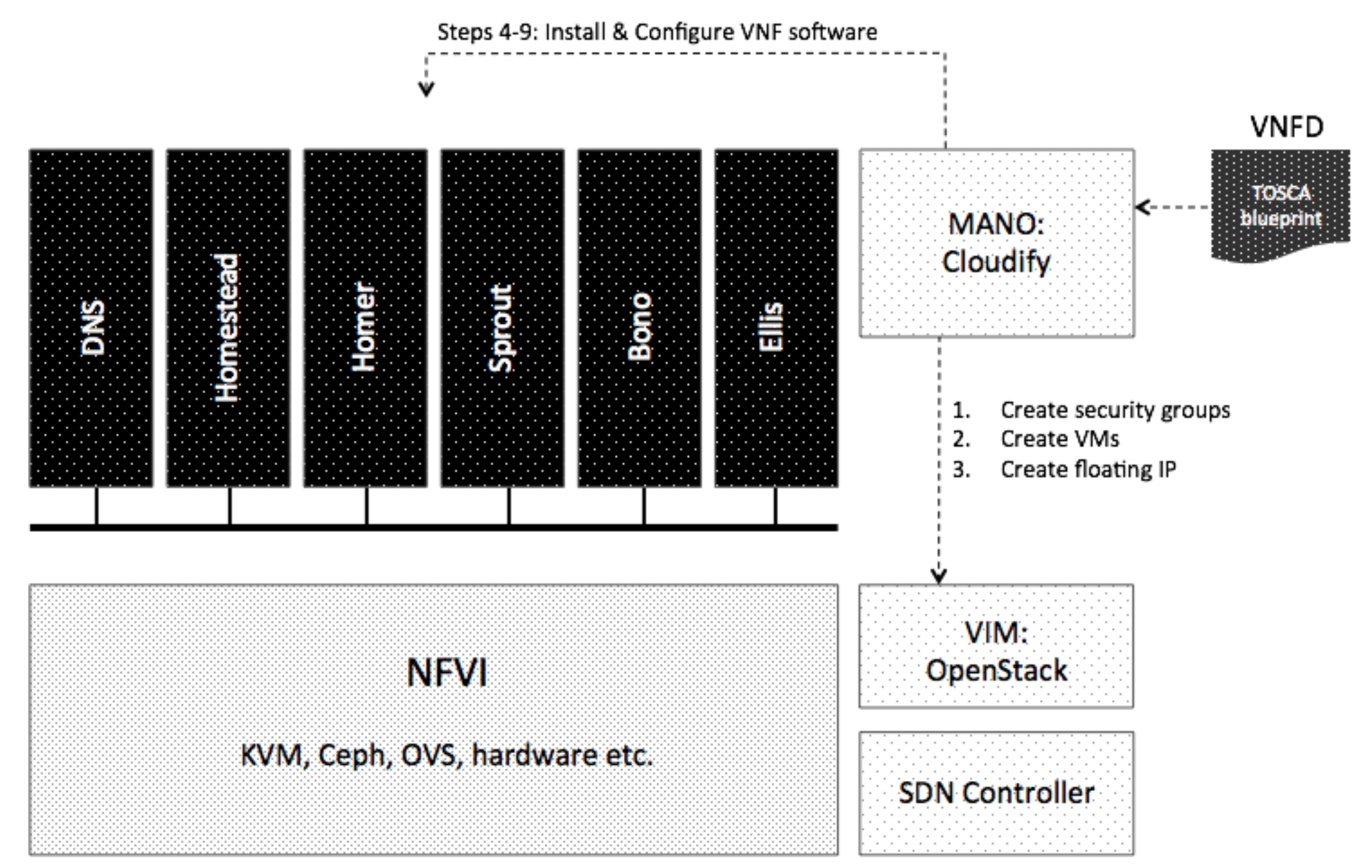
Even with a shortage of IT workers, some employers are still discerning in their hiring requirements and are either seeking certified candidates or offering to pay for their employees to become certified.
The Linux Foundation’s 2017 Open Source Jobs Report finds that half of hiring managers are more likely to hire a certified professional, while 47 percent of companies are willing to help pay for employees’ certifications. Meanwhile, 89% of hiring managers find it difficult to find open source talent.
The demand for skills relating to cloud administration, DevOps, and continuous integration/continuous delivery is fueling interest in training and certifications related to open source projects and tools that power the cloud, according to the report. Workers find certification important, too. In fact, 76 percent of open source pros say certifications are useful to their careers.
Existing cloud certifications, such as the Certified Kubernetes Administrator exam, are expected to help address the growing demand for these skills, the report states.
Why certifications are important
Demand for certifications is on the rise. Half of hiring managers prioritize finding certified pros; 50 percent also say they are more likely to hire a certified candidate than one without a certification, up from 44 percent in 2016, according to the Open Source Jobs report. And there’s been a big jump in companies willing to pay for employees to become certified. Nearly half say they’re willing to pay, up from one-third a year ago.
Here’s why. Some employers believe training alone is not enough and perceive that overall, certified IT pros make great employees, according to a CompTIA report. In fact, the study finds 91 percent of employers view IT certifications as a differentiator and say they play a key role in the hiring process.
Then there is perception. “Certifications make a good first impression,” the CompTIA report observes, and there is the belief that certified IT employees are more confident, knowledgeable and reliable, and perform at a higher level. While not specific to a particular technology, a whopping 95 percent of employers in the CompTIA study agree IT certifications provide a baseline set of knowledge for certain IT positions.
Only 21 percent say they definitely would not pay for certifications, down from 30 percent last year, the Open Source Jobs report finds.
The good news for IT professionals is that with certification, pay premiums have consistently grown over the past year. Areas in which IT pros receive higher pay, include: information security; application development/programming languages; databases; networking and communications; and systems administration/engineering – skill sets that are among the hardest to fill.
Dice’s annual salary survey finds salaries for Linux professionals are in line with last year, at over $100,000 annually – higher than the average $92,000 for tech pros nationally.
Formal training and/or certifications are a priority for hiring managers looking for developers (55 percent, compared to 47 percent who said so in 2016) and for Systems Administrators (53 percent vs. 47 percent last year).
Trending skills and certifications in high demand
In its 2018 Salary Guide, Robert Half Technology lists the most highly sought tech skills and certifications in North America. Among them are: .NET, Agile, and Scrum certifications. For application development work, businesses are seeking certifications and skills in areas including PHP and LAMP (Linux, Apache, MySQL, and Perl/Python). In networking and telecommunications, Linux/Unix administration is in high demand as well as in technical services, help desk, and technical support.
Meanwhile, 76 percent of professionals find certifications are useful to their careers, mainly to demonstrate technical knowledge to potential employers (reported by 47 percent of respondents), and 31 percent say that certifications generally make them more employable.
Although salary, not surprisingly, is the biggest incentive for switching jobs (82 percent), certification opportunities is an incentive for 65 percent of respondents in the Open Source Jobs report.
Download the full 2017 Open Source Jobs Report now.